The introduction of my PhD thesis (2012) reaffirms that the word “privacy” is semantically overloaded, and summarizes a few of the key interpretations and perspectives. This includes the taxonomies of privacy by Alan Westin (1964) and Daniel Solove (2005). For my own purposes I post the relevant parts below. Hopefully it is useful to others as well.
[…]
[T]he word privacy suffers from semantic overload. Privacy can be approached from various perspectives, such as ethics, law, sociology, economics and technology (the latter being our perspective). Before focusing on how to measure, we first want to know what to measure and why. To that end, this introductory Chapter has a broad scope and first considers multidisciplinary aspects of privacy. A property shared between various perspectives is that privacy entails some desire to hide one’s characteristics, choices, behavior and communication from scrutiny by others. Such ‘retreat from wider society’ may be temporary, such as when visiting the bathroom, or more permanent, such as when opting for hermit life or choosing to publish using a pseudonym. Another prevalent property is that privacy entails some desire to exercise control over the use of such information, for example to prevent misuse or secondary use. Phrases commonly associated with privacy include “the right to be let alone”, meaning freedom of interference by others [ref: S. D. Warren and L. D. Brandeis. The right to privacy. Harvard Law Review, IV, December 1890]; “the selective control of access to the self or to one’s group”, meaning the ability to seek or avoid interaction in accordance with the privacy level desired at a particular time [ref: I. Altman. The environment and social behavior: privacy, personal space, territory, crowding. Brooks/Cole Pub. Co., 1975]; and “informational self-determination”, meaning the ability to exercise control over disclosure of information about oneself. The latter phrase was first used in a ruling by the German Constitutional Court related to the 1983 German census.
It is unlikely that any reasonable person would accept that all their thoughts, feelings, social relations, travels, communication, physical appearance including the naked body, sexual preferences, life choices and other behavior are knowable by anyone, at any time, without restriction — not least because that exposes them beyond their control to yet unknown people and institutions in yet unknown situations, i.e., pose a risk to their personal security and/or feeling of security.
At the same time, transparency of the individual can reduce risk, including collective risk. In the Netherlands, for example, the welfare-issuing Dutch municipalities have commissioned an organization named Stichting Inlichtingenbureau to counter welfare fraud via linkage and analysis of data about welfare recipients. Stichting Inlichtingenbureau can link welfare registry data to judicial registry data for purposes of stopping fugitive convicts from receiving welfare and informing the Dutch Ministry of Justice of the whereabouts of fugitives. Nowadays, Stichting Inlichtingenbureau also provides services to the Dutch water control boards (‘waterschappen’), Regional Coordinationpoints Fraud Control (‘RCF Kenniscentrum Handhaving’), Regional Reporting and Coordination function school dropouts (RMC), Central Fine Collection Agency (CJIB), Social Insurances Bank (SVB), and bailiffs [Footnote: According to a trend report issued by the Dutch governmental Research and Documentation Centre (WODC), 368 bailiffs and 414 junior bailiffs were active during 2005: https://www.wodc.nl/images/ob247-summary_tcm44-59825.pdf].
Risk reduction can, at least theoretically, pervert into seeking a risk-free society [ref: J. Holvast. Op weg naar een risicoloze maatschappij? De vrijheid van de mens in de informatiesamenleving. Leiden, 1986] and suppress behavior that is permissible but deviates from social norms. Not unlike the ‘chilling effect’, i.e. the stifling effect that overly broad laws [ref: L. Forer. A Chilling Effect: The Mounting Threat of Libel and Invasion of Privacy Actions to the First Amendment. Norton, 1989.], profiling and surveillance [ref: G. Horn. Online searches and offline challenges: The chilling effect, anonymity and the new FBI guidelines. New York University Annual Survey of American Law 60 N.Y.U., 735, 2004-2005.] are claimed to have on legitimate behavior such as exercising the constitutional right to free speech. Although we are unaware of scientific evidence for such causality (it is beyond our expertise), one only needs to consider practices in certain parts of the world to be convinced that (being aware of) the possibility of being scrutinized can cause a person to change her behavior. Think of a person not expressing a dissenting opinion near a microphone-equipped surveillance camera at work or in a public space where that person would otherwise have done so; or a person not traveling to the red light district, even if one needs to be there for some other than the obvious reason, due to fear of abuse of data collected by real-time vehicular registration systems and public transport smart card systems. Perhaps both find alternative ways to achieve their goal; but it seems unwise to assume that that is always the case, and then disregard the effects that technology and human-technology interaction can have on the human experience to which privacy is essential. The need for risk reduction and accountability at the collective level can be at odds with the need for privacy at the personal level; what constitutes the ‘right’ balance will depend on context.
Certain personal information is considered ‘sensitive’ because it can, and has often shown to, catalyze stigmatization, social exclusion and oppression: ethnicity, religion, gender, sexuality, social disease, political and religious preference, consumptive behavior, whether one has been victim or culprit of crime, and so on. The need for private life, also in terms of being able to keep certain information to oneself, is therefore neither new nor temporary, and worthy of defense. Reducing misunderstanding and mistreatment through means of public education, especially the promotion of reason, critical thinking and empathy, is one step forward; forbidding discrimination through legislation is another; enabling privacy impact assessment and control over the disclosure of information about oneself, especially sensitive information, the topic of our thesis, is yet another.
The rise of social media and ubiquitous computing does not imply the ‘end’ or ‘death’ of privacy. Rather, as Evgeny Morozov paraphrased from Helen Nissenbaum’s book [ref: H. Nissenbaum. Privacy in context: technology, policy, and the integrity of social life. Stanford Law Books, 2010] in The Times Literary Supplement of March 12th, 2010: “the information revolution has been so disruptive and happened so fast (…) that the minuscule and mostly imperceptible changes that digital technology has brought to our lives may not have properly registered on the social radar”. In her 2.5-year ethnographic study of American youngsters’ engagement with social network sites, Boyd observed that youngster’s “developed potent strategies for managing the complexities of and social awkwardness incurred by these sites” [ref: D. Boyd. Taken Out of Context: American Teen Sociality in Networked Publics. PhD thesis, University of California, Berkeley, Berkeley, CA, USA, 2008.]. So, rather than privacy being irrelevant to them, the youngsters found a way to work around the lack of built-in privacy. In conclusion: privacy is not dead. At worst, it is in intensive care, beaten up by overzealous and sometimes careless use of technology. It will return to good health, even if merely for economical reasons [ref: M. Bangemann. Europe and the global Information Society (Bangemann report), 1994].
It remains unclear when the desire to retreat first emerged, and even whether it is only found in humans. From an evolutionary or biological perspective, privacy might be explained by the claim that hiding oneself and one’s resources from predators and competitors in the struggle for existence is beneficial for survival. The desire to retreat, then, is perhaps as old as the struggle for existence itself. This notion, however, seems very distant from common ideas about privacy. With more certainty, sociological study has traced the emergence of withdrawal from classical antiquity — distinguishing between ‘religiously motivated quest for solitude’ and the ‘lay quest for private living space’ [ref: D. Webb. Privacy and Solitude in the Middle Ages. Hambledon Continuum, London, 2007]. Alternatively, privacy can be conceived as a means to ‘personal security’.
[…]
From a legal perspective, one of the early and most well-known comprehensive works on privacy dates from 1890, when US Supreme Court Justices Warren and Brandeis published “The Right to Privacy” in the Harvard Law Review [ref: S. D. Warren and L. D. Brandeis. The right to privacy. Harvard Law Review, IV, December 1890]. In the 20th century, Castle Doctrine emerged in legislation of self-defense of one’s private space — its name referring to the proverb “a man’s house is his castle” [ref: R. A. Merkt, A. L. Mchose, and A. Chiappone. The “new jersey self-defense law”. Assembly No. 159, State of New Jersey, 213th Legislature, 2008].
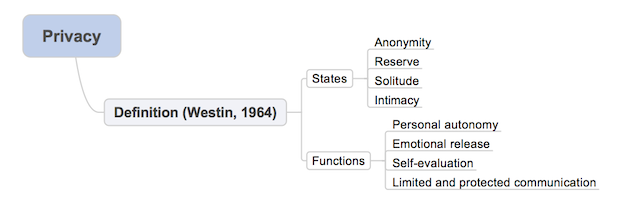
During the 1960s, Westin, a legal scholar who focused on consumer data privacy and data protection, described four ‘states’ and four ‘functions’ of privacy [ref: A. Westin. Privacy and freedom. Atheneum, New York, 1970]. Figure 1.1 shows our mind-map of his conceptualization.
The four functions, or ‘ends’, or ‘reasons’ for privacy that Westin distinguishes are personal autonomy, e.g. regarding decisions concerning personal lifestyle; emotional release, e.g. of tensions related to social norms; self-evaluation, e.g. extracting meaning from personal experiences; and limited and protected communication, e.g. disclosing information only to trusted others. The four states, or ‘means’ to privacy that Westin distinguishes are anonymity, e.g. ‘hiding’ within a group or crowd; reserve, e.g. holding back certain communication and behavior; solitude, e.g. seeking separation from others; and intimacy, e.g. seeking proximity to a small group.In the same era, Prosser, a legal scholar focusing on tort law, wrote that what had emerged from state and federal court decisions involving tort law were four different interests in privacy, or ‘privacy torts’ [ref: W. L. Prosser. Privacy. California Law Review, 48(3), 1960]:
- intrusion upon the plaintiff’s seclusion or solitude, or into his private affairs;
- public disclosure of embarrassing private facts about the plaintiff;
- publicity which places the plaintiff in a false light in the public eye;
- appropriation, for the defendant’s advantage, of the plaintiff’s name or likeness.
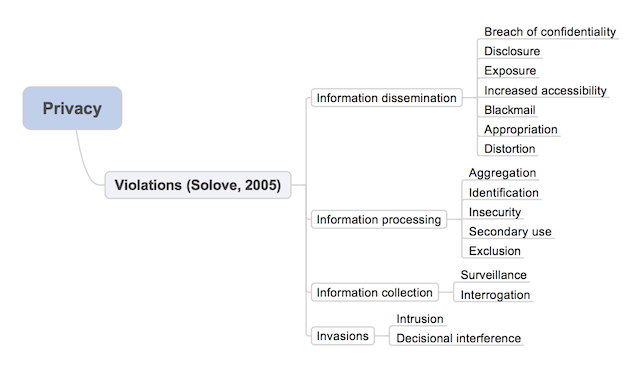
More recently, in 2005, Solove, a legal scholar focusing on privacy, proposed a taxonomy of privacy violations that, unlike Prosser’s, does not only focus on tort law [ref: D. J. Solove. A Taxonomy of Privacy. University of Pennsylvania Law Review, 154(3):477–560, Jan. 2005]. Figure 1.2 shows a map of that taxonomy.
Solove describes the violations as follows. Categorized under information processing activity: aggregation comprises the combination of information about a person; identification comprises linking information to specific persons; insecurity comprises lack of due diligence protecting (stored) personal information from leaks and improper access; secondary use comprises the re-use of information, without subject’s consent, for purposes different from the purpose for which it was originally collected; exclusion comprises not allowing the subject to know or influence how their information is being used. Categorized under information collection activity: surveillance comprises “watching, listening to, or recording of an individual’s activities”; interrogation comprises various forms of questioning or probing for information. Categorized under information dissemination activity: breach of confidentiality comprises “breaking a promise to keep a person’s information confidential”; disclosure comprises revealing (truthful) information that “impacts the way others judge [the] character [of the person involved]”; exposure comprises revealing “another’s nudity, grief, or bodily functions”; increased accessibility comprises “amplifying the accessibility of information”; blackmail comprises the threat to disclose personal information; appropriation comprises the use of the subject’s identity “to serve the aims and interests of another”; distortion comprises the dissemination of “false or misleading information about individuals”. Categorized under invasions: intrusion comprises acts that “disturb one’s tranquility or solitude”; decisional interference comprises “[governmental] incursion into the subject’s decisions regarding private affairs”.
[…]
Recommended additional reading:
- Helen Nissenbaum’s conceptualization of privacy as contextual integrity (2004) built from context-relative informational norms.
- An excellent primer (.pdf, 2012) on privacy by Jaap-Henk Hoepman and Marc Lieshout.
EOF
One thought on “The many interpretations and perspectives of privacy”