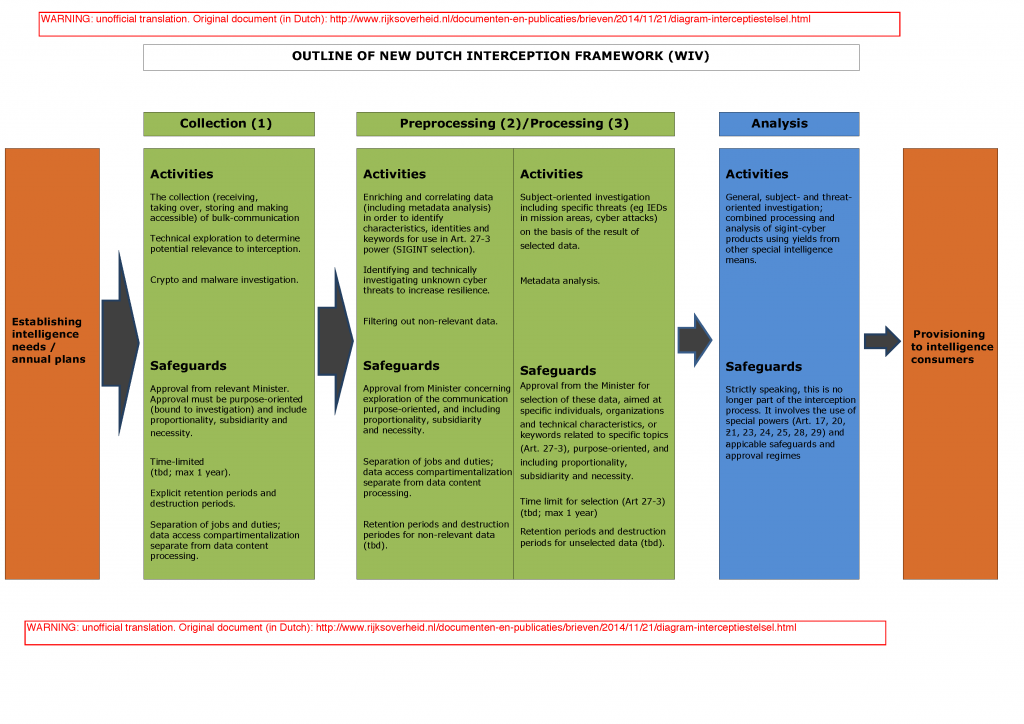
UPDATE 2015-10-30: the Dutch government announced it has decided on a bill that revises the invalidated Telecommunications Data Retention Act of 2009. Changes are proposes to take into account recent Dutch and European jurisprudence: access to retained data will now require prior approval from a magistrate (specifically, in Dutch, a “rechter-commissaris”), and only be permitted regarding offenses that allow temporary remand (and thus only regarding offenses that carry a maximum penalty of four or more years imprisonment). The status of the bill can be viewed here (in Dutch). The government will consult the Council of State and then submit the bill to parliament.
UDPATE 2015-01-30: answers (.doc, in Dutch) to Parliamentary questions from MP Verhoeven, Schouw, Van Tongeren and Gesthuizen about the illegality of the Dutch telecommunications data retention act.
UPDATE 2014-12-19: handy table (.pdf, by the Open Rights Group in cooperation w/EDRi) showing status of data retention in various EU Member States following the ECJ ruling.
UPDATE 2014-12-16: Dutch government: Let’s keep data retention mostly unchanged (Bits of Freedom)
TL;DR: the Dutch government upholds the existing Dutch implementation of the EU Data Retention Directive and proceeds with its proposal for ANPR data retention. The Dutch government does, however, cater to the ECJ’s ruling through some cosmetic changes.
On November 17th, the Dutch government responded (.pdf, in Dutch) to the ECJ’s rejection of the EU Data Retention Directive in April. The response addresses consequences of the ruling for the current telecommunications data retention legislation in the Netherlands, as well as for the ANPR data retention bill that is being prepared.
The remainder of this post consist of a translation of the entire 18-page response as sent to Parliament by the Minister of Security and Justice, Ivo Opstelten. Translation was done as literal as possible; interpretation is limited to phrases that necessitate non-literal translation to avoid confusion. Questions and suggestions for correction/improvement are welcomed. Hyperlinks and parts in [] are mine.
Relevant reading: Evaluation report on the Dutch implementation of the EU Data Retention Directive (post of July 17th 2014 on evaluation report published at the end of 2013).
WARNING: this is an unofficial translation.
1. Introduction and background
On April 8th 2014, the Court of Justice of the European Union (hereafter: Court of Justice) in the cases of Digital Rights Ireland and Seitlinger ruled on the validity of directive 2006/24/EC (hereafter: data retention directive). This concerns court cases C-293/12 and C294/12 [sic; latter should be “C-594/12”]. The data retention directive was ruled invalid by the Court of Justice.
Following this ruling, the Dutch State Secretary for Security and Justice during the parliamentary Question Time on April 8th stated that Parliament would be informed as soon as possible, to be expected within eight weeks, about the consequences of this ruling for the data retention law in the Netherlands (Handelingen Tweede Kamer 2013/2014, nr. 72, item 2).
On April 10th 2014, through letter 2014Z06389/2014D13189, the Permanent Committee for Security and Justice asked me to respond to this ruling of the Court of Justice, and more specifically to address the following questions:
- Which (Dutch) laws are based on this directive? What does the ruling mean for the binding and execution/implementation of these laws?
- Does the Dutch law on retention of telecommunications data need to be updated?
- Does the ruling have consequences for telecommunications companies operating in the Netherlands and for other companies subject to this Dutch law? If so, what consequences?
- What consequences does the ruling have for broad methods of storage of personal data by the government that currently exist and/or that the government intends to introduce?
- What are the consequences of the ruling for the secret services?
On April 23rd 2014, through letter Kamerstukken I, 2013/14, 31 145, Y, the Permanent Committee for Immigration and Asylum / JHA Council [in Dutch: “vaste commissie voor Immigratie en Asiel / JBZ-Raad”] expressed that it considers the retention and storage of traffic and location data in accordance with the data retention directive to be a very extensive and severe infringement in fundamental rights, and asked the State Secretary for Security and Justice to state what measures will be taken, and when revocation or suspension of the data retention law concerning traffic and location data will take place.
During the General Meeting on the processing and protection of personal data on April 24th 2014, the Permanent Committee for Security and Justice and the Permanent Committee for European Affairs requested that the Dutch Data Protection Authority (CBP) and the Council of State be asked for advice about the ruling of the Court of Justice. The State Secretary for Security and Justice responded by stating that can not be ruled out that the eight week term would not be met (Kamerstukken II 2013/14, 32 761, nr. 64, pages 14-15 and 20). During the General Meeting on the JHA Council of June 4th 2014, the State Secretary of Security and Justice stated that some delay occurred and that he hoped to be able to provide more clarity by July (Kamerstukken II 2013/14, 32 317, nr. 246, pages 19 and 23).
On behalf of the government, the present letter addresses the consequences of the ruling of the Court of Justice in the cases of Digital Rights Ireland and Seitlinger for the data retention law concerning telecommunications data, and the Parliamentary questions following that ruling.
For the purpose of careful decision-making I have, through a letter dated May 20th 2014, requested the Vice President of the Council of State, on the basis of Article 21a, first member, of the Law on the Council of State, to provide me information about the question what the possible consequences of this arrest are to the national legislation on retention of telecommunications data for the purpose of investigation and prosecution of offenses. On July 17th 2014 I received a letter with this information from the Advisory Division of the Council of State. In the course of establishing the present response, this information has been taken into account. On the basis of this response, a draft bill has been developed, that will be submitted to the CBP for advice. The CBP’s advice will thereby be sought on the consequences of the ruling of the Court of Justice for the data retention law in the Netherlands. This offers the opportunity to currently inform you, the Parliament, about the government’s response following the aforementioned ruling of the Court of Justice, and to publish the information from the Advisory Division of the Council of State. The latter information has been added as an appendix to the present letter. The draft bill for changing the Telecommunications Act [official English translation available here] and the Code of Criminal Procedure concerning providing public electronic communication services has also been added to this letter for information.
2. The data retention directive
The data retention directive concerns the retention of telecommunications data. The directive was intended to harmonize Member States’ national regulations, and to establish requirements for providers concerning the retention of data generated or processed by them, so as to ensure that those data were available for investigation and prosecution of serious crime, as defined in national legislation of the Member States. This concerned so-called traffic data: data about the use of telecommunication by individuals. The data retention directive required Member States to ensure that certain categories of telecommunications data were retained for a minimum of six months and up to two years. The categories of data to be retained were listed in the directive. It concerned data about the number of the caller and the called party, time, duration, and location of the start of the connection. The contents of a conversation or text message were not included in the directive. Historic traffic data about internet concerned, among others, the email address of the sender and recipient, and the traffic data of digital telephony. The contents of conversations, messages or emails, keywords that have been entered in a search engine and IP addresses of internet pages [sic] that were visited, were not included in the directive. The data retention directive established that Member States would implement regulations to ensure that data retained under this directive are only provided to competent authorities in certain well-defined cases, in accordance with national law (Article 4).
3. Dutch legislation implementing the data retention directive (current law)
The data retention directive was implemented in the Netherlands by means of the Telecommunications Data Retention Act of 2009 [in Dutch: ” Wet bewaarplicht telecommunicatiegegevens”, Stb. 2009, 333], that got enacted per September 1st 2009, and the Telecommunications Bill of July 6th 2011 that changes the retention period for telecommunications data concerning internet access, internet-based email and internet-based telephony. Furthermore, the implementation of the data retention directive was followed by a change of the Decision Telecommunications Data Security of 2009 [in Dutch: “Besluit beveiliging gegevens telecommunicatie”, Stb. 2009, 350].
The Telecommunications Data Retention Act of 2009 provides an extension and change of Section 11 (protection of personal data) and Section 13 (lawful interception) of the Telecommunications Act (Tw). Providers of public telecommunication networks and services retain data, insofar these data are generated or processed within the context of the offered networks or services, for the purpose of investigation and prosecution of serious crime. The retention period is twelve months for data about telephony from a land-line or mobile network. For certain forms of internet-based telephony, such as VoIP, the functionality is so coherent with traditional telephony that the same retention period applies to such services. For internet data (internet access, internet-based email and other forms of internet telephony), the retention period is six months (Article 13.2a, third member, Tw). The categories of data to be retained are equal to those of the European directive. Following that directive, the retention period for so-called location data is increased from three to twelve months (Article 13.4, third member, Tw). This is for the purpose of data analysis to be able to trace data of holders of so-called prepaid cards (Decision Special Number Data Collection; in Dutch: “Besluit bijzondere vergaring nummergegevens”).
General criminal investigatory powers
Access to retained data is regulated in the Code of Criminal Procedure (and the Intelligence and Security Act of 2002). The Code of Criminal Procedure grants a public prosecutor [in Dutch: “officier van justitie”] the power to demand traffic data (Article 126n and Article 126u Sv). The use of this power requires suspicion of a crime for which remand is possible, or a reasonable suspicion that offenses are planned or committed in organized context that comprise a serious breach of the law. Besides the prosecutor, the investigating officer is itself authorized to demand so-called user data; this concerns data about name, address, place, number, and type of service. This concerns a far more limited category of data than the category of data that can be obtained on the basis of the power to demand traffic data. The use of this power is therefore not limited to cases involving serious offenses. The use of this power requires suspicion of an offense or a reasonable suspicion that offenses are plannen or committed in organized context (Article 126na and Article 126ua Sv).
Special powers for counter-terrorism
Lastly, the prosecutor and investigating officer have special powers concerning counter-terrorism. In case of indications of a terrorist offense, the prosecutor is authorized to demand traffic data (Article 126zh Sv). Besides the prosecutor, the investigating officer is itself authorized to demand user data in case of indications of a terrorist offense (Article 126zi Sv).
If an exploratory investigation is aimed at preparing the investigation of terrorist offenses, the prosecutor can, in support of the investigation, demand data files from public and private institutions for the purpose of having the data therein processed (Article 126hh Sv). The data files can be searched for certain profiles and patterns of act of individuals that are of importance to counter-terrorism. The use of this power requires a written warrant from the judge [in Dutch: “rechter-commissaris”]. This concerns a general power that can also be used on providers of telecommunication services or networks.
Data retained on the basis of the Telecommunications Data Retention Act are subject to the Dutch Data Protection Act [in Dutch: “Wet bescherming persoonsgegevens”, or “Wbp”] and Section 11 of the Telecommunications Act. The personal data that can be requested by the police and that are then processed for the purpose of investigation into offenses, are subject to the Police Data Act [in Dutch: “Wet politiegegevens”]. The oversight on compliance with the rules is exercised by the Telecom Agency (AT; in Dutch: “Agentschap Telecom”) of the Ministry of Economic Affairs and the Authority for Consumers and Markets (ACM), in cooperation with the Dutch Data Protection Authority (CBP). Providers are required to take suitable technical measures to protect the retained data from unauthorized use, to ensure that the data is only accessed by specially appointed persons, and that the data are immediately destroyed after the retention period (Article 13.5, second and third member, Tw). The Decision Telecommunications Data Security provides further rules concerning the protection of retained data. This concerns the requirement to take security measures to prevent unauthorized access, the screening of persons that have access to the data, and the destruction of data after the retention period.
4. The ruling by the European Court of Justice
In the ruling of April 8th 2014, the Court of Justice — at the request of the Irish High Court and the Austrian Verfassungsgerichtshof — examined the validity of the European directive, in particular in the light of two fundamental rights of the Charter of Fundamental Rights of the European Union [hereafter: “Charter”], namely the right to privacy (Article 7 of the Charter) and the right to family life (Article 8 of the Charter). These rights build on human rights and fundamental rights (ECHR). The Court of Justice finds that the European data retention directive is retrospectively invalid. The Court of Justice thereto considers that the data to be retained can provide very accurate clues about the private life of those whose data are retained, such as habits of everyday life, permanent or temporary places of residence, daily or other movements, the activities carried out, the social relationships of those persons and the social environments frequented by them. It is not inconceivable that this eventually affects the right to freedom of speech that is laid down in Article 11 of the Charter (item 28). The infringement of the rights by the directive is wide-ranging and particularly serious (item 37).
The Charter requires that every infringement of rights and freedoms laid down in the Charter must be provided for by law and, subject to the principle of proportionality, limitations of these rights and freedom may be made only if they are necessary and genuinely meet objectives of general interest recognized by the Union or the need to protect the rights and freedoms of others (item 38). The principle of proportionality requires that a EU regulation is “appropriate” to pursuing legitimate objectives of that regulation, and does not exceed limits to what is appropriate and necessary. According to the Court, the retaining of telecommunications data can be considered appropriate to pursue the objective of the directive (item 49).
The Court of Justice then examines whether the EU regulation lays down clear and precise rules governing the scope and application of the measure in question and imposing minimum safeguards so that the persons whose data have been retained have sufficient guarantees to effectively protect their personal data against the risk of abuse and against any unlawful access and use of that data. The review of certain paragraphs of the data retention directive leads the Court of Justice to find that the directive does not lay down clear and precise rules governing the extent of the interference with the fundamental rights enshrined in Articles 7 and 8 of the Charter (item 65). It was concluded that the EU legislator exceeded the limits imposed by compliance with the principle of proportionality in the light of Articles 7, 8 and 52(1) of the Charter (item 69). The considerations underlying this ruling will be discussed below, in the discussion of the cabinet’s response concerning the consequences of this ruling for national legislation. The European Commission left open the possibility to propose a new directive till after the formation of the new commission. It is yet uncertain whether the new European Commissioner will take an initiative on this.
5. Consequences of the ruling to the Dutch legislation concerning data retention of telecommunications data
The precise meaning of the potential consequences of the ruling of the Court of Justice for the Dutch legislation concerning the retention of telecommunications data requires a diligent analysis. The Court of Justice first finds that retention of telecommunications data for the purpose of preventing offenses and fighting crime in fact serves an objective of general interest (item 44). Taking into account the increasing importance of electronic means of communication, the retention of these data are a valuable instrument to authorities in criminal investigations. The retention of such data is therefore appropriate for attaining the objective pursued by the data retention directive (item 49). The Court of Justice then considers that the regulation does not lay down clear and precise rules governing the scope and application of the measure in question, and does not impose minimum safeguards so that the persons whose data have been retained have sufficient guarantees to effectively protect their personal data against the risk of abuse and against any unlawful access and use of that data (item 54). The Court of Justice finds that the directive entails a wide-ranging and particularly serious interference with the fundamental rights laid down in Article 7 and 8 of the Charter, without such an interference being precisely circumscribed by provisions to ensure that it is actually limited to what is strictly necessary (item 65).
The consequences of the ruling by the Court of Justice will now be discussed, as well as Parliamentary Questions that followed the ruling.
5.1. Can the Dutch legislation concerning retention of telecommunication data be upheld?
The first question is whether the Telecommunications Data Retention Act can be upheld, now that the data retention directive has been ruled invalid. The government answers that question in the affirmative. The Dutch law was established legally, on the basis of applicable procedures. The Advisory Division concludes that the mere fact that the Court of Justice found the data retention directive to be invalid, does not imply that national legislation that implements that directive is invalid. The Dutch legislator has a general authority to establish rules. The Dutch law already contains safeguards that exceed those of the data retention directive, such as the rules in the Code of Criminal Procedure about access to retained data. The established legislation must however be, or made to be, in accordance with the (new) explanation of existing fundamental rights concerning the protection of private life and the protection of personal data. This will be discussed later.
5.2. Is mandatory retention of telecommunications data necessary?
The government is convinced of the importance and indispensability of telecommunications data retention. Data retention ensures that certain telecommunications data are available to investigate and prosecute serious offenses. Existing powers in the Code of Criminal Procedure also allow demanding data from providers of telecommunication services, but without legally required data retention, it is not certain that those data are available at the provider. Rapid technological developments in communication technology make it uncertain whether the data, that are important to investigation and prosecution, are being processed by the providers for their own business operations and whether such data is available for investigation and prosecution. In addition to the data retention, the specific retention period is of vital importance, because the length of data retention directly affects the availability of data for investigation and prosecution. Specifically at a later stage it can turn out that certain telecommunications data are of importance to an investigation, without it being clear at the time of retention of the data that individuals are involved in serious offenses. Numerable examples can be given. One concerns an accomplice to two violent robberies in Rotterdam, in which the accomplice was not identified until ten months later. Another example concerns a rape in which the long-term investigation eventually led to the perpetrator, partially thanks to traffic data that proved that the suspect was in proximity of the victim at that time. Yet another example concerns international investigation into child abuse, in which children younger than ten years old were very severely abused. More than hundred IP addresses belonged to Dutch persons. But none of these cases could be investigated because the retention period had expired, meaning that the IP address could no longer be associated with an individual. A reference can be made to the publication [.pdf] by the European Union about the necessity of data retention in the European Union.
5.3. Does the Dutch legislation concerning retention of telecommunications data need to be changed?
The next question is whether the Telecommunications Data Retention Act must be changed, given the ruling by the Court of Justice. The government also answers this question in the affirmative. National rules on retention of telecommunications data are relevant to the free movement of services within the European Union and are, now that the data retention directive has been ruled invalid, within the scope of directive 2002/58/EC (ePrivacy Directive). On the basis of this directive, Member States can establish rules for retention of telecommunications data, if so necessary, reasonable and proportional in a democratic society to safeguard legitimate interests, including the prevention, investigation and prosecution of offenses. Member states can thereto take measures to retain data for a limited period for those aims. These measures must be in accordance with the community law, including the principles, as meant in the Charter and the ECHR. Because data retention is within the scope of the ePrivacy Directive (Article 15(1), ePrivacy Directive) and thus within the scope of European Union law, it also is within the scope of the Charter.
The Advisory Division finds that the Telecommunications Data Retention Act transposes the rules disputed by the Court of Justice, and that review of the Telecommunications Data Retention Act against the Charter leads to the concludes that this law, as well as the data retention directive, violate Article 7 and Article 8 of the Charter. It follows that national legislation must be changed insofar it is not in accordance with the Charter. The Dutch government subscribed to this view. Later on I will discuss the various requirements established by the Court of Justice for retention of telecommunications data, and point out on which aspects the Telecommunications Data Retention Act needs to be changed to meet the requirements of the Charter.
5.3.1. Requirements to the legislation
The Court of Justice considers that a legitimate objective is pursued through data retention, namely the fight against serious crime (item 44 and 51). This, by itself, does not mean that the directive is in accordance with the Charter. The data retention must, according to the Court of Justice, be limited to what is strictly necessary (item 52) and clear and precise rules must exist. Then the Court considers that the data retention directive applies to all persons, all means of electronic communication and all traffic data, without any differentiation, limitation or exception being made in the light of the objective of fighting against serious crime (item 57). The Court of Justice thereby considers that the data retention directive even applies to persons for whom there is no evidence capable of suggesting that their conduct might have a link, even an indirect or remote one, with serious crime (item 58).
Based on these considerations of the Court of Justice, the Advisory Division concludes that a European regulation must clearly and precisely describe which categories of data, of which historic means of communication, of which persons are strictly necessary for prevention, investigation or prosecution of crime and must thus be retained by providers of telecommunication. Herein, clues must exist that a relation exists between the behavior of persons whose data are retained and serious crime. Following this, I note that legally required data retention serves to ensure that historic telecommunications data are available, if in hindsight it turns outs that such data is relevant to investigation and prosecution. If a crime is committed, it can be important to determine whom the victim or suspect has been in contact with prior to the crime, such that the perpetrators and accomplices can be identified. If the data of these persons can not be retained prior to the crime, there would be no point in asking such a question. The retention of certain data about all citizens is thus necessary, as it is not possible to differentiate between suspected and unsuspected citizens beforehand. Unlike the Advisory Division, the government is of the opinion that such considerations by the Court of Justice should be interpreted in their interrelationships/coherence. If the view of the Advisory Division would be true that each of the safeguards mentioned by the Court of Justice must be met separately, then the mere fact that data of citizens is retained, without any indication that their behavior relates to serious crime, would be sufficient to invalidate the data retention directive. The Court of Justice, however, rules that taking all considerations into account (“Having regard to all the foregoing considerations”), the EU legislature has exceeded the limits imposed by compliance with the principle of proportionality in the light of Articles 7, 8 and 52(1) of the Charter (item 69). The ECHR jurisprudence also does not support the view that such data storage is not permitted. That consideration of the Court of Justice must, according to the Dutch government, be explained in that the fact that the directive does not require a link between data retention and personal behavior can be a very serious limitation of personal life of those involved, but that the seriousness of that limitation can be mitigated by appropriate guarantees and safeguards for careful methods of storing, processing and accessing the data. The required mitigation can be achieved through some mutually reinforcing changes of the law. The seriousness of the infringement on personal life necessitates very critical review of the nature and extent of data retention based on the Telecommunications Data Retention Act, as well as the applicable guarantees and safeguards. These aspects will be discussed later. Successively, the questions whether retention periods and categories of data must be changed will be discussed, and whether the rules concerning access to the data and protection and security need to be changed.
5.3.2. Retention periods and categories of data to be retained
The Court of Justice considers that the data retention directive, having a minimum retention period of six months, does not differentiate between the categories of data set out in Article 5 of the directive on the basis of their possible usefulness for the purposes of the objective pursued (item 63). Furthermore, the directive does not state that the determination of the period of retention — set at between a minimum of 6 months and a maximum of 24 months — must be based on objective criteria in order to ensure that it is limited to what is strictly necessary (item 64).
The Advisory Division notes that the Court of Justice requires that the retention period is differentiated to the various categories of data on the basis of their possible usefulness for the purposes of the objective pursued or according to the persons concerned. Such distinction is not made in the Telecommunications Data Retention Act of 2009, which only differentiates between data about telephony and data about internet, email and internet telephony.
Following this, the retention periods for telecommunications have been reconsidered. The framework provided by Article 15 (1) of the ePrivacy Directive was taken into account. Indeed, now that the data retention directive has been ruled invalid, a national telecommunications data retention law can only be determined within the framework of the ePrivacy Directive. That directive does not define the meaning of “limited period”, as meant in Article 15 (1). The measures must be appropriate for, and strictly necessary within a democratic society, and must include adequate safeguards conform the ECHR (preamble of the ePrivacy Directive, item 11). This implies a change of Article 13.2a, third member, and Article 13.4, third member, of the Telecommunications Act. In determining the retention period, both privacy and necessity to prosecution must be taken into account. The government thus finds that the retention periods should remain unchanged. That is, a retention period of six months for internet data and twelve months for telephony data. To limit the infringement on personal life resulting from data retention as much as possible, it is proposed that the rules concerning access to the data and protection and security be changed. This will be elaborated on later. The requirement that on the basis of objective criteria it must be clearly and precisely described per category of data for what period it must be retained by telecommunications providers ignores the purpose of the essence of data retention. That essence is that certain telecommunications data must be available for the investigation of serious crime. If the data are strictly necessary for that objective, then retention of them is applicable. If the data are not strictly necessary for that objective, then this is not the case. Differentiation between categories of data is irreconcilable with this. The requirement can however be met in other ways. Distinction can be made in the period of availability of data for the investigation of serious crime, in the sense that the period of access increases depending on the seriousness of the crime. Thus an objective criterion, namely the seriousness of the crime, can be used to differentiate in availability of data for crime prevention. This implies change of Article 126n and Article 126u of the Code of Criminal Procedure.
5.3.3. Access to retained data
The Court of Justice considers that the directive does not provide an objective criterion that limits access to the data by competent authorities. The directive refers to serious crime, as defined by each Member State in its national law (item 60). The directive does not contain contain substantive and procedural conditions relating to the access of the competent national authorities to the data and to their subsequent use. That is left up to Member States (item 61). In particular, the directive does not provide an objective criterion to limit the number of persons who have access, the subsequent use of the data, to what is necessary in the light of the objectives pursued. Above all, the access by the competent national authorities to the data retained is not made dependent on a prior review carried out by a court or by an independent administrative body following a reasoned request of those authorities (item 62).
In the Netherlands, direct access to the database is already strictly regulated. Only authorized employees of the providers have access to the retained data. The provisioning of the data by providers of public telecommunications networks and services for the investigation and prosecution of crime is governed by the rules laid down in the Code of Criminal Procedure. On the basis of those rules, the public prosecutor can, in case of suspicion of a crime that permits remand or in case of a reasonable suspicion that crimes are being planned or committed in organized context that constitute a serious breach of the law, request traffic data in the interest of the investigation. A list of crimes that permit remand is included in Article 67(1) of the Code of Criminal Procedure. Hence, unlike in the data retention directive, access to the retained data for investigation and prosecution is limited to cases involving serious crime. Following the ruling by the Court of Justice, the government intends to add new safeguards aimed at further limiting of access to retained data. Firstly by the introduction of a system of differentiation in access to the data,and by introducing advance judicial review.
The system of differentiation is designed to establish that the full retention period, unlike now, is only used in case of the most severe category of offenses that carry very long prison sentences. In lighter offenses, for which remand is possible but that do not carry very long prison sentences, the data can be requested during a shorter period. In the latter case, data may be subject to data retention, but the public prosecutor can not request the data for investigation of a certain offense because the offense is not serious enough to justify access to the data.
In addition, a judicial review is proposed. Currently, as said, the authority to request traffic data is reserved for the public prosecutor. By making access to retained data subject to advance judicial review, it is better ensured that the data are only used in cases where sufficient reason exist to do so, and that the privacy of citizens is protected. To that end, the Code of Criminal Procedure will lay down that the demand for retained data depends on an advance authorization from a judge [in Dutch: “machtiging van de rechter-commissaris”].
Furthermore, in case of suspicion of a crime or a reasonable suspicion that crimes are planned or committed in organized context that constitute a serious breach of the law, the investigating officer can, in the interest of the investigation, request historic user data (Article 126na and Article 126ua Sv). A similar power applies in case of indications of a terrorist offense (Article 126zi Sv). This involves data concerning name, address, postal code, place, number and type of service of a user of a communication service. Here, “type of service” means the type of telecommunication service that is used, such as land-line or mobile telephony, internet, or types within these services, such as telefax. The use of these powers is possible in case of suspicion of a crime, and is not limited to cases of serious crime. The government believes that the category of user data, as mentioned, constitutes a far more limited category of data. From these data, no precise conclusions can be drawn about the private life of the persons about whom the data is retained, as the Court of Justice finds to be the case for retention of traffic data based on the data retention directive (item 27). The government believes that the retention of user data must be assessed different from retention of traffic data, and sees no reason to change the current legislation concerning this.
5.3.4. Data protection and data security
The Court of Justice considers that the data retention directive does not provide sufficient guarantees for effective protection against the risk of abuse and against any unlawful access and use of that data. The directive does not provide specific rules adapted to the vast quantity of data that must be retained, or to the sensitive nature of these data and the risk that they will be used unlawfully. The directive does not lay down a specific obligation on Member States to establish such rules (item 66). The directive does not ensure that a particularly high level of protection and security is applied by providers by means of technical and organizational measures, but permits those providers in particular to have regard to economic considerations when determining the level of security which they apply, as regards the costs of implementing security measures. In particular, the directive does not ensure the irreversible destruction of the data at the end of the data retention period (item 67). The data retention directive also does not require the data in question to be retained within the European Union, with the result that it cannot be held that the control, explicitly required by Article 8(3) of the Charter, by an independent authority of compliance with the requirements of protection and security, as referred to in the two previous paragraphs, is fully ensured (item 68).
Following these considerations, the government notes that the Dutch Data Protection Act (Wbp) and the Telecommunications Act (Tw) already have safeguards and rules, on the basis of which provides must take appropriate technical and organizational measures for safety and security of the networks and services they offer (Article 13 Wbp and Article 11.3 Tw). These norms implement European rules. Providers can take the state of the art of technology and the economical costs into account, but paramount is that the measures are appropriate, considering the risks involved in the processing of the data that is to be protected. Hence, the safety and security of the networks and services must be ensured at all times. The Data Protection Authority (CBP) monitors compliance with Article 13 Wbp and Article 11.3 Tw. Besides the CBP, also the ACM is tasked with monitoring compliance with Article 11.3 Tw. In addition to those requirements, the providers must take appropriate technical and organizational measures to protect the data against destruction, loss, change, unauthorized storage, processing, access or disclosure, to ensure that only specially authorized persons access the data, and to destruct the data after the retention period (Article 13.5, second member, Tw). Providers have no possibility to take economic costs into account. The Decision Telecommunications Data Security [in Dutch: “Besluit beveiliging gegevens telecommunicatie”] lays down rules for the security of access to the retained data. Moreover, the Telecommunications Act, as noted by the Advisory Division, provides an obligation for immediate destruction of the data (Article 13.5, third member, Tw). The Telecom Agency (AT) [in Dutch: “Agentschap Telecom”] monitors compliance with Article 13.5 Tw. The Minister of Economic Affair has sent the report “Measurement data retention 2013” [in Dutch: “Meting dataretentie 2013”] to the Parliament in a letter dated May 16th 2014 (Kamerstukken II 2013/14, 26 643, nr. 313). This report aims to provide insight into compliance with the Telecommunications Data Retention Act. From the periodic and individual reviews of the providers it is apparent that they generally comply with the legal regulations concerning the storage of data and privacy of their customers. In the light of the legal regulations and the experiences with those regulations in practice, the government believes that the Dutch regulation in general meets the requirements of the Court of Justice concerning protection and security of retained data. On some aspects the governments considers it necessary to make changes.
Further rules on the security of retained data have been included in the Decision Telecommunications Data Security. The retained data may only be accessible for a limited number of employees of the provider. Given the sensitivity of these data, it stands to reason that data retained for the purpose of investigation and prosecution are fully protected from unauthorized access. The government will investigate whether encryption of these data can take place.
The Advisory Division pointed out that Dutch law, like the data retention directive, does not provide an obligation to store retained data within the European Union, and therefore it is currently not fully ensured, as the Court of Justice requires, that the CBP can oversee security and protection of retained data.The Court of Justice explicitly links to the purpose thereof: to ensure that the data are sufficiently secured and protected. In response to this, the government intends to change the regulation in the Telecommunications Act, such that providers are obliged to retain and process the data within the European Union. Monitoring of compliance with the norms concerning protection and security of retained data, that to a large extent follow from European rules, can thereby be improved.
Monitoring of compliance with Section 13 of the Telecommunications Act is done by the Minister of Economic Affairs and the CBP. The Minister therefore uses officials of the Telecom Agency. The supervisory task of the Minister of Economic Affairs in no way limits the supervisory powers of the CBP concerning personal data. Supervision by the Telecom Agency is currently designed as supervision of the system. That means that the Telecom Agency assesses business processes and their guarantees. On the basis of the Telecommunications Act, the Telecom Agency is however not authorized to request traffic data that must be retained by providers on the basis of the Telecommunications Data Retention Act. The Telecom Agency thus lacks a useful instrument to be able to carry out this part of the supervisory task. The government intends to change the Telecommunications Act, such that the Telecom Agency, as a supervisory authority, can get access to telecommunications data retained or provided by providers, if and insofar that is necessary for oversight. That change will allow better oversight on lawful and careful processing of the retained data, including the actual destruction of it. Better monitoring of compliance with the legal rules will cater to the ruling of the Court of Justice.
6. Consequences for telecom companies operating in the Netherlands and other companies
The measures proposed in section 5 of this letter will have consequences for the business operations of internet and telecom providers operating in the Netherlands. The obligation to store data within the European Union can have consequences for the business operations and costs of the providers. The precise effects and costs will be investigated in cooperation with the private sector. From the perspective of the internal market, it is not to be expected that the presently proposed measures will carry disproportional obstacles. It must also be taken into account that the requirements following from the ruling of the Court of Justice apply to all Member State, such that these will have an equal consequence to the national laws concerning data retention for the purpose of investigation and prosecution of serious crimes.
In the letter to Parliament sent by the Minister of Economic Affairs on May 16th 2014 concerning the report “Measurement data retention 2013”, it was noted that besides six large telecom providers, 337 SME providers have obligations concerning data retention and privacy. It was stated that the number of request of investigative services address to these group of smaller parties is limited (ca. 2 percent). This group carries, considering its limited business size, relatively more costs and efforts to meet the requirements concerning data retention and privacy. The application and compliance with rules concerning data retention proved complex especially for this group of providers. It will thus be considered in what way this group of providers can be spared, by providing ways to comply with Telecommunications Data Retention Act as efficiently as possible.
It will be discussed with providers what possible practical solutions exist to comply with the legal obligations in a way that avoids disproportionate costs and efforts wherever possible.
7. Consequences of the ECJ ruling to the Dutch intelligence and security services
The data retention directive left Member States the necessary room for regulating access to retained telecommunications data. The Member States were to ensure that retained data would be provided to competent national authorities only in well-defined cases and in accordance with national law.
On the basis of Article 28 of the Dutch Intelligence & Security Act of 2002 (Wiv2002), the AIVD and MIVD are authorized to request data about a user and their traffic data from providers of public telecommunication networks and services. On the basis of Article 13.4, first member, of the Telecommunications Act of 2009, these providers are obliged to immediately comply with such requests. Nothing changes in this. In the context of renewal of the Wiv2002, the government will further discuss possible consequences of the Court of Justice for the activities of the intelligence and security services.
8. What consequences does the ruling have for broad forms of storage of personal data currently carried out by the government and that the government still intends to introduce?
Following questions from the Permanent Committee for Security and Justice, I note that “broad forms of storage of personal data” apparently refers to legal rules concerning the storage of data for criminal purposes about persons about whom (at that time) no indications exist of involvement in crimes. Such storage exists in the proposal to change the Code of Criminal Procedure concerning the regulations of the recording and storing of ANPR data by the police (33 542), also known as the ANPR bill. The ANPR bill provides a legal basis for storing certain license plate data of all vehicles passing a camera. This concerns license plate number, a photo of the vehicle, the time and location. The retention period is four weeks. The data can be used for investigation of a criminal offense that permits remand and for arresting of a fugitive or convict. The data can only be used by an authorized investigating officers, for the purpose of the investigation. Linking retained ANPR data to databases outside the police, to identify persons for the purpose of investigation (‘data mining’), is not possible. The text of the proposed Article 126jj of the Code of Criminal Procedure excludes this.
The ANPR bill has an important similarity to the data retention directive, as license plate numbers are retained of all passing vehicles, including those of persons who’s behavior at the time of recording is not linked to serious crime. The Advisory Division points this out and notes that it is up to the legislator and, eventually, the judge, to provide a definitive judgement of this proposal, but to take into account the possibility that this sort of data storage will be considered to be a violation of proportionality or as irrelevant and excessive, assuming the criminal purpose of the storage. However, significant differences exist between the data retention directive, which is subject of the ruling of the Court of Justice, and the ANPR bill. This firstly concerns the nature of the data to be retained. Different from telecommunications data, that can provide a more all-encompassing of citizen behaviors, license plate data cannot provide very accurate indications about the private life of those whose data is retained, such as the habits of everyday life, permanent or temporary places of residence, daily or other movements, the activities carried out, the social relationships of those persons and the social environments frequented by them. The license plate data only provide insight into where a vehicle at a certain date and time was registered by a camera. Although on the basis of license plate data insight is possible into the location of a vehicle on certain dates or times, no insight is obtained in relations between persons. The nature of these data makes them less invasive to personal life. It is of vital importance that the ANPR bill provides a retention period of four weeks, which is significantly shorter than the retention period included in the data retention directive of up to two years for telecommunication traffic data. In addition, license plate data are collected at public roads. Drivers of vehicles can know and expect that their vehicle can be registered by the police at public roads for the purpose of law enforcement. Also taking into account the principle of “reasonable expectation of privacy” of those involved, the collection and retention of license plate data must be assessed differently than the collection and retention of telecommunications data.
Unlike the retention of telecommunications data, the access to retained ANPR data does not require advance review by a court or an independent administrative body, as meant by the Court of Justice (item 62). I believe that, now that the infringement on personal life is less serious than the retention of telecommunications data, it is not strictly necessary to also provide such a safeguard in retention of ANPR data. As with telecommunications data, ANPR data is retained specifically for the purpose of investigation and prosecution of crime. Considering that similarity, I intend to require advance approval from a public prosecutor for access to retained ANPR data. The requirement of advance authorization from a public prosecutor also applies to the use of other special powers, such as systematic observations, the systematic collection of information, and infiltration. Because the use of these powers constitute a breach on the privacy of those involved that is greater than the retention of ANPR data — a warrant for observation can for instance permit observation of a person’s behavior for three months — I believe that such a requirement amply satisfies the requirements following from the Charter. The Code of Criminal Procedure will thus regulate that the request of retained ANPR data requires advance approval from the public prosecutor. This means that the proposed Article 126jj of the Code of Criminal Procedure will be changed, such that an authorized investigating officers can only request retained ANPR data after obtaining approval from the public prosecution, for the purpose of investigating a serious crime of arresting a fugitive.
Access to retained ANPR data for the purpose of investigation and prosecution of crimes is limited to cases involving a suspicion of a crime the permits remand, or reasonable suspicion that crimes are being planned or committed in organized context that constitute a serious breach of the law. In the light of the requirements set by the Court of Justice to access to retained telecommunications data, the government finds that this regulation meets the requirements to be set based on the ECHR or — insofar applicable — the Charter of Fundamental Rights of the European Union.
As I stated earlier, in a letter dated April 10th 2014 (Kamerstukken II, 2013/14, 33 542, nr. 13), I firmly believe the legislative proposal — certainly with a further limitation of access to the data — is well within the limits of Article 8 of the ECHR and — insofar applicable — Article 7 and 8 of the Charter.
9. In conclusion
The government thus intends to change the national legislation concerning retention of telecommunications data, such that:
- the public prosecutor can only issue a warrant to obtain telecommunications data following advance approval from a judge. This means that Article 126n/u of the Code of Criminal Procedure will be changed;
- access to the data for the purpose of investigation and prosecution of serious crimes will be differentiated based on the seriousness of the crime. This means the Article 126n/u of the Code of Criminal Procedure will be changed;
- it will be examined whether telecommunications data retained for the purpose of investigation and prosecution of serious crimes can be encrypted so that they are protected from unauthorized access. This can result in a change of the Decision Telecommunications Data Security;
- providers will be obligated to retain data within the European Union. This means that Article 13.2a and Article 13.5 of the Telecommunications Act will be changed;
- the Telecom Agency, as a supervisory body, can get access to telecommunications data that are retained or provided by providers, with the objective of better oversight on the processing and destruction of the retained data. This means that Article 18.7, second member, of the Telecommunications Act will be changed;
These changes will be included in a proposal to change the Telecommunications Act and the Code of Criminal Procedure, that will soon be released for public consultation.
Furthermore, the government intends to change the ANPR data retention bill, such that:
- the authorized investigating officer can only access retained ANPR data following advance approval from the public prosecutor, for the purpose of investigating a serious crime or arresting a fugitive. This means that the proposed Article 126jj of the Code of Criminal Procedure will be changed.
This change will be included in an Amending Letter for the ANPR bill, that will soon be sent to Parliament.
EOF