On October 14th 2014, the Dutch government published (in Dutch) the fifth edition of the “Cyber Security Assessment Netherlands” trend report, aka “CSAN-2015” (in Dutch: “CSBN-5”) . Its aim is “to offer insight into developments, interests, threats and resilience in the field of cyber security over the period from April 2014 to April 2015”. The publication was established using information from the following sources:
- The various ministries
- Military Intelligence and Security Service (MIVD)
- Defence Computer Emergency Response Team (DefCERT)
- General Intelligence and Security Service (AIVD)
- National High Tech Crime Unit, Dutch National Police
- Public Prosecution Service
- Representatives of the critical infrastructure sectors and NCSC partner organisations
- National Coordinator for Security and Counterterrorism (NCTV)
- National Management Organisation for Internet Providers (NBIP)
- Internet Standards Platform (Dutch: “Platform Internetstandaarden”)
- Bits of Freedom
- ICT Netherlands
- Dutch Payments Association
- Confederation of Netherlands Industry and Employers (VNO-NCW)
- Scientific institutions
- Universities
- Experts in the field of cyber security
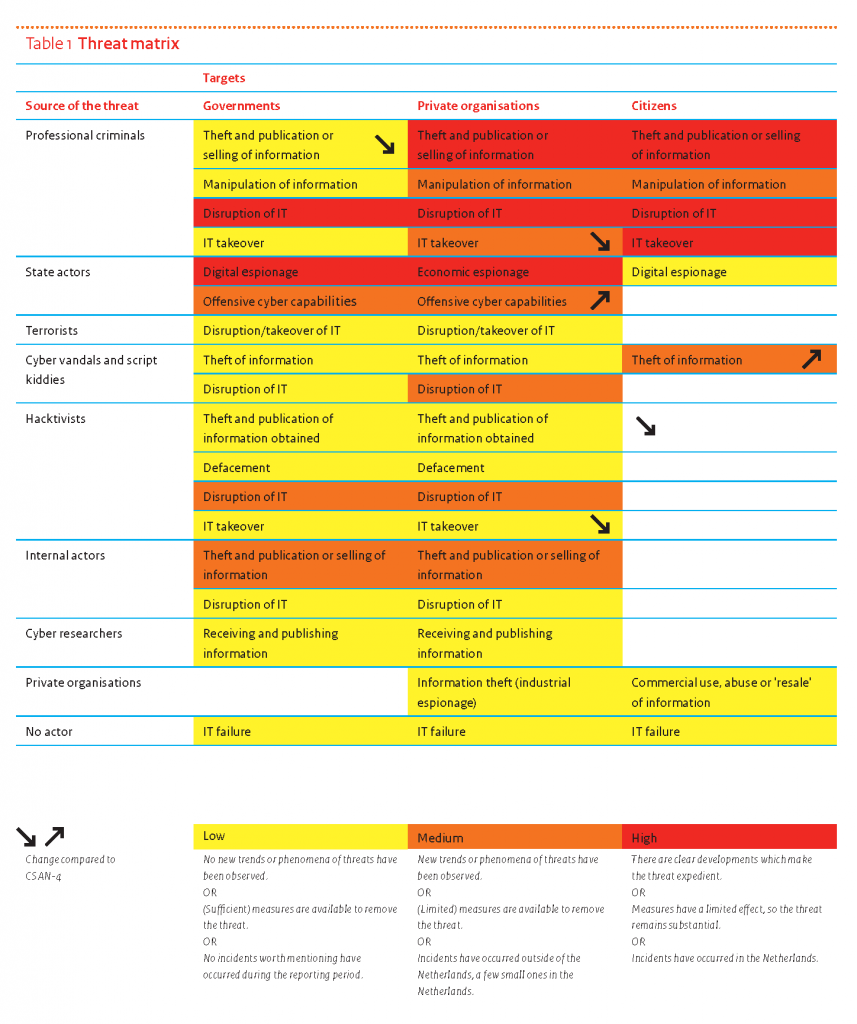
On November 17th, the government published an English translation. Here is the updated threat matrix table (click image to enlarge):
And here is the summary (~2300 words):
Summary
The Cyber Security Assessment Netherlands (CSAN) is published annually by the National Cyber Security Centre and drawn up in close collaboration between public and private parties. The aim is to offer insight into developments, interests, threats and resilience in the field of cyber security over the period from April 2014 to April 2015.
The focus of the CSAN lies on the developments in the Netherlands, but important developments abroad have also been included. The CSAN is a factual description, with guidance based on insights and expertise from government departments, critical infrastructure sectors and the academic community. For this CSAN, the NCSC has renewed its collaboration with a large number of parties, both public parties (e.g. the police, intelligence and security services and the Public Prosecution Service), academic institutions and private parties (such as the critical infrastructure sectors).
Over the past few years, more attention has been paid to the dependence on IT. Countries attach increasing importance to the internet and IT becomes indispensable. More and more insight is gained into the number of incidents, which also allows for more targeted measures being taken to increase cyber security, for larger and smaller organisations. Phishing and cryptoware, however, continue to pose a threat to the Netherlands as a whole.
Core findings
Cryptoware and other ransomware constitute the preferred business model for cyber criminals
Criminals use cryptoware (ransomware) increasingly often in order to achieve their goals. Unlike other common malware, such as Remote Access Tools (RATs), criminals use cryptoware to block access to data using encryption. The willingness of people and organisations to pay the criminals results in high average proceeds per target for criminals. That is why they can make relatively large investments per infection. More advanced forms, for example aimed at web applications, have also been identified. The popularity of the use of ransomware and, in particular, cryptoware will further increase in the next few years.
Geopolitical tensions manifest themselves increasingly often in (impending) digital security breaches
States and other actors that seem to act in line with the interests of these states increasingly use digital attacks and cyber operations. The aim is to represent their interests and to influence geopolitical relations or developments. Digital attacks are an attractive alternative and addition to conventional military and espionage means. Their scope and impact are large and the costs and risks are low. In the past year, conflicts, attacks or political issues were often the reason for digital attacks. It is often difficult to trace back the actor who carried out the actual attack, and to determine the extent to which a state actor played a leading role in the attack.
Phishing is often used in targeted attacks and can barely be recognised by users
Phishing (‘fishing’ for login and other user data) plays a key role in carrying out targeted digital attacks. Users are hardly able to recognise phishing e-mails in targeted attacks. A successful phishing campaign gives attackers access to internal networks of organisations and the information stored on these networks. Means to make authentic e-mail recognisable as such (e.g. digital signatures, Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) and Domain-based Message Authentication, Reporting and Conformance (DMARC)) are only used in practice to a limited extent. This ensures that phishing continues to be a low-threshold and effective method of attack for attackers.10
Availability becomes more important as alternatives to IT systems are disappearing
Important social processes come to a standstill if the corresponding IT systems and analogue alternatives are unavailable. The phasing out of analogue alternatives to IT systems therefore makes the availability of these systems even more important. This is especially true if these IT systems support important social processes such as transport, financial transactions or energy supply. The measures that banks have taken against DDoS attacks show that it is possible to take effective measures in order to increase availability of digital facilities. However, organisations often wait to take such measures until IT systems have already experienced availability problems.
Vulnerabilities in software are still the Achilles heel of digital security
Software is a crucial part of our digital infrastructure, because software opens up the possibilities of hardware and the ever growing amount of data. Software suppliers in 2014 again released thousands of updates in order to repair vulnerabilities in their software. Organisations sometimes do not install updates due to the obstacles they encounter when installing them. As long as the updates have not been installed, parts of their network will continue to be vulnerable. Such vulnerabilities allow actors penetrating networks via phishing or zero-day
Key questions
The key questions of this CSAN 2015 are:
- What events or what activities by which actors could affect IT interests, what tools do they use and what are the developments in this respect? (threats)
- To what extent is the Netherlands resilient to vulnerabilities in IT, could these lead to an impact on IT interests and what are the developments in this respect? (resilience)
- Which Dutch interests are being adversely affected and to what degree, by restrictions of the availability and reliability of IT, breach of the confidentiality of information stored in IT or damage to the integrity of that information, and what are the developments in this respect? (interests)
Insight into threats and actors
Table 1 provides insight into the threats that the various actors have posed over the period between April 2014 and April 2015 to the targeted ‘governments’, ‘private organisations’ and ‘citizens’.
Criminal organisations and state actors continue to pose a threat to these three target categories. This threat has become more specific. For most organisations, the manifestations of less advanced actors form a smaller part of the total than before. In some cases, the red colour conceals that a high threat level can increase as well. The paragraphs on criminals and state actors in Chapter 2 discuss this in more detail.
Manifestations
Growth in number of incidents with ransomware and cryptoware continues
The rise of ransomware and cryptoware in 2013 continued in 2014 and 2015, also in the Netherlands. Ransomware and cryptoware is malware that holds IT systems ‘hostage’ by making them unavailable and demands a ransom. Cryptoware also encrypts the data that is stored. Various cryptoware variants caused many incidents over the past period. Infections were caused by, for example, Cryptolocker, CryptoFortress, Cryptowall and CTB locker. In the Netherlands, organisations are often affected by such infections.
DDoS attacks continue to take place, but measures prevent disruptions more often
DDoS attacks remain a concern in the Netherlands. After the wave of DDoS attacks in early 2013, service providers have invested in measures to prevent these attacks. Frequent and serious DDoS attacks on websites of governments and private organisations are still being detected. The origin of the problems is therefore still in place. As a result of the increased attention to anti-DDoS measures, however, services are often not disrupted.
Espionage attacks, which become more and more frequent, start with spearphishing
In the past year, the Netherlands was dealing much more often with digital espionage attacks that posed a threat to national security and economic interests. Research conducted by the AIVD and MIVD showed that, in 2014, Dutch government institutions were often the target of advanced digital espionage attacks. Most of these attacks were carried out using spearphishing e-mails containing attachments infected with malware or links to malware websites.
Threats: actors
The biggest threat continues to be posed by professional criminals and state actors
The digital skills of criminals continue to develop. Last year saw, for example, several digital attacks by criminals which were notable for their good organisation, accurate implementation and technical sophistication. Moreover, more countries carry out digital attacks on or via the infrastructure of Dutch organisations. The biggest digital espionage threat is posed by foreign intelligence services.
Terrorists do not yet pose a serious threat, but their capabilities are, however, growing
Although the potential of terrorist actors in the digital field is growing, they do not yet pose a serious threat due to their limited technical capabilities. There are no indications of a specific threat against the Netherlands. In the context of digital attacks carried out by terrorists, the biggest threat is currently posed by jihadism. So far, digital attacks with jihadist motives in the Netherlands were limited to small-scale attacks that required little knowledge and manpower.
Conflicts, attacks and incidents provide a context for digital attacks
Various actors use national and international conflicts, attacks and incidents as a reason to carry out digital attacks. In the past year, for example, many digital attacks and cyber operations were observed which can be placed in a geopolitical context, such as the malware attacks related to the conflict in the Ukraine. It is often very difficult to link these attacks to parties. Both state actors and activist hackers with patriotic motives have the intentions and tools to carry out these attacks.
Threats: Tools
Dissemination of cryptoware is a lucrative criminal activity
The proceeds generated by criminals using cryptoware are high. Approximately 10 percent of Dutch reporting parties say they have paid criminals in order to regain access to files. The proceeds probably amount to several hundreds of euros per person per payment. The relevant criminals do their best to expand their market by looking for other means to infect (such as SD cards, USB sticks and network sources) and by using other encryption methods (for example by corrupting systems over a long period).
Phishing, or spearphishing in particular, is the most frequently used tool for targeted attacks
The parties who carried out various targeted attacks that were discovered in the past period often succeeded in their efforts by making use of spearphishing, with a phishing e-mail being sent to one person or a limited group of persons. Apart from spearphishing, actors also still use classic phishing as a tool. The Netherlands is a particularly popular target for phishers. This may have to do with the relatively good economic situation and the strong euro.
Malvertising continues to pose a danger to internet users
Advertisements have been incorporated in many websites, which sometimes have a high number of visitors. One malicious ad may therefore have a large impact in a short period of time. If a user opens a website that contains a malicious ad, this will often result in all kinds of vulnerabilities in the user’s system being exploited fully automatically, so without any further user interaction. Nowadays, cyber criminals also abuse advertisement networks to attack specific user groups. They use on-line advertising auctions to this end.
Resilience: vulnerabilities
Publicity campaigns for vulnerabilities make prioritising more difficult
The past reporting period shows a development with much more publicity regarding technical vulnerabilities. Various sectors have reported that these publicity campaigns involve a risk: due to the great deal of attention that is paid to individual vulnerabilities, the issues of the day may divert attention from structural solutions. In that case, management will not always make decisions based on the correct information and will receive the impression that security officers are insufficient prepared.
Raising awareness alone will not help prevent phishing
The quality of phishing texts has become even better. Individual users can hardly be blamed for falling victim to them. Technical measures to prevent phishing are, however, still used up to a limited extent. For example, less than 10 percent of government domain names are protected against phishing attacks using the open standards DKIM, SPF and DMARC.
Resilience: measures
Security of open source software comes at a price
The Heartbleed vulnerability showed that open source software is not automatically safer, even if it is used frequently. The publicity surrounding this bug resulted in large internet companies joining forces in April 2014 in the Core Infrastructure Initiative. The initiative invests in the open source basic infrastructure of the internet and improves the basic security of the internet. However, it currently only covers a small part of the open source projects responsible for the infrastructure of the internet. This kind of financing is not available for other projects.
Recruitment in cyber security: many vacancies, few people
The labour market for cyber security professionals has, for some time now, been characterised by a large difference between the supply of and demand for (technical) cyber security professionals. The number of vacancies is increasing; the government has also actively recruited staff members in this area over the past period. Organisations often experience difficulties in filling job vacancies. This applies to technical cyber security positions in particular.
Detection capacity is essential for the discovery of advanced attacks
Advanced attacks, so-called Advanced Persistent Threats (APTs), are difficult to detect. These attacks, aimed at organisations in various sectors, often circumvent existing security measures. It often takes months or years before the attacks are discovered, which may result in a serious extent and impact of the damage for the organisations affected. Although an increasing number of organisations have special software to protect them against APTs, it appears that the prevention of such attacks is mostly unexplored territory for many organisations.
Interests
New areas of application result in vulnerabilities and debate
More IT is installed in cars, aircraft and other means of conveyance. This requires attention for the security of this IT. For a security problem in an entertainment system should not affect the operation of the vehicle. A lack of security may, in such a case, even have fatal consequences. Such risks may also arise if the software used contains bugs, a licence expires or a network service is no longer available. Security often has no priority in the development of such new applications.
Interests of critical infrastructure are large but stable
The interests protected by the critical infrastructure remain large but show little change. Consultations with representatives of organisations in those sectors have made this evident. Although the security of information and systems each time creates new challenges, the underlying motivations for security have hardly changed.
Alternatives to IT systems are disappearing
If IT systems that support social processes are not available, it is, in a growing number of cases, no longer possible to rely on analogue alternatives. The availability of these IT systems thus becomes more important: failure is not an option. At the same time, the underlying technology is more complex than with analogue systems. Moreover, these systems can be attacked more easily if they can be accessed via the internet.
EOF