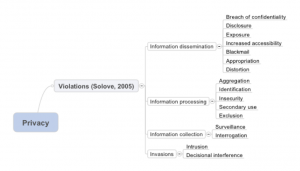
In 2005, legal scholar Daniel J. Solove published A Taxonomy of Privacy. For my own purposes I made a mindmap of his taxonomy and list below the descriptions of the distinct privacy violations.
Categorized under information dissemination activity:
- breach of confidentiality conveys “breaking a promise to keep a person’s information confidential”;
- disclosure conveys revealing (truthful) information that “impacts the way others judge [the] character [of the person involved]”;
- exposure conveys revealing “another’s nudity, grief, or bodily functions”;
- increased accessibility conveys “amplifying the accessibility of information”;
- blackmail conveys the threat to disclose personal information unless the blackmailers demands are met;
- appropriation conveys the use of the subject’s identity “to serve the aims and interests of another”;
- distortion conveys the dissemination of “false or misleading information about individuals”.
Categorized under information processing activity:
- aggregation conveys the combination of information about a person;
- identification conveys linking information to specific persons;
- insecurity conveys lack of due diligence protecting (stored) personal information from leaks and improper access;
- secondary use conveys the re-use of information, without subject’s consent, for purposes different from the purpose for which it was originally collected;
- exclusion conveys not allowing the subject to know or influence how their information is being used.
Categorized under information collection activity:
- surveillance conveys “watching, listening to, or recording of an individual’s activities”;
- interrogation conveys various forms of questioning or probing for information.
Categorized under invasions:
- intrusion conveys acts that “disturb one’s tranquility or solitude”;
- decisional interference conveys “[governmental] incursion into the subject’s decisions regarding private affairs”.
Read Solove’s original paper (.pdf) before applying this taxonomy; there’s more substance to it than this short blogpost seeks to represent.