On October 28th, the third Cyber Security Assessment Netherlands (CSAN-3) was published(.pdf, in English) by the Dutch National Cyber Security Center. These are the core findings of CSAN-3:
- Several trends show considerable IT dependence, rising fast due to advances such as hyperconnectivity, cloud computing and the ease with which the internet is used as an enabler. The potential impact of incidents occurring is all the more obvious.
- Digital espionage and cyber crime remain the biggest threats to both government and the business community. This concerns:
a) Digital espionage originating from a foreign state, aimed at government and the business community. Activities have been identified originating from, among other countries, China, Russia, Iran, and Syria.
b) IT takeovers by criminals by means of malware infections, aimed at government, the business community and citizens. Criminals are becoming more daring in their ways of earning money quickly, for example, phoning citizens, or confronting them with shocking images in ransomware.
c) Manipulation of information (fraud) by criminals, aimed at the business community, most obviously internet banking fraud, which victimises both banks and citizens. - States can develop and deploy advanced tools, while cyber criminals continue to develop their existing tools. Clearly visible in the past year has been the rise of a commercially available cyber services sector, ‘cyber crime as a service’, which offers far easier access to criminal tools to various parties.
- Citizens, businesses, and governments alike are regular victims of botnets and ransomware. Malware can mutate so quickly that anti-virus programs are unable to even detect its presence. Although botnets are mainly used to manipulate (financial) transactions, certain incidents (such as Pobelka) show that the collateral damage of information stolen through botnets can be enormous.
- The IT sector continues to be vulnerable. Following a few years of reduced levels, the number of openly published vulnerabilities in software is increasing again. Cloud services, mobile services and innovative devices all result in new vulnerabilities.
- The end-user is burdened with a big responsibility for security, but more often than not has little influence or even knowledge of the vulnerabilities he confronts in the devices and services.
- Public and private parties are starting up initiatives, both separately and together, to increase digital resilience and in anticipation of the ever-increasing dependence on IT and changing threats. The effectiveness of these initiatives can only be measured in the long term.
- Disruption in the IT sector is displayed publicly, particularly when it comes from Distributed Denial of Service (DDoS) attacks. Resilience has been inadequate at times, which led to a decline in the availability of online services provided by organisations. In addition, DDoS attacks disrupted basic services such as DigiD and iDeal, and this had a chain effect on governmental organisations and businesses that use these services. It is not clear who is behind the DDoS attacks.
- As yet, a broad group of organisations is unable to implement important basic (technical) measures, such as patch and update management or a password policy. Where individual organisations do have their basic security well organised, it appears that shared services and infrastructure are still vulnerable, which in turn leads to a risk for interests that transcend particular organisations.
- The inherent dynamics of cyber security demand a new approach. Static information security measures are no longer sufficient; organisations need greater insight into threats (detection) and need the capacity to deal with the threats (response).
Furthermore, the report states:
In conclusion, a) dependence on IT by individuals, organisations, chains and society as a whole has grown; b) the number of threats aimed at governments and private organisations has risen, mainly originating from states and professional criminals; and c) digital resilience has remained more or less at the same level. Although more initiatives and measures are being taken, they are not always in step with the vulnerabilities, and basic security measures have not always been put in place.
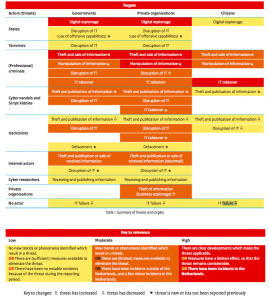
Table 1 gives insight into the threats that various actors use to launch attacks on governments, private organisations, and citizens. […]