On November 4th, the Dutch National Cyber Security Research Agenda II (.pdf, in English), or `NCSRA-2′, was published. The NCSRA is a “guiding document” for the calls for academic (primarily) and non-academic cyber security research proposals in the Netherlands. The first NCSRA, or `NCSRA-1′, was published (.pdf, in English) in 2012.
The old NCSRA-1 (2012) defined seven research themes, and focused almost entirely on defense:
- Identity, Privacy and Trust Management
- Malware (defensive)
- Forensics
- Data and Policy Management
- Cybercrime and the underground economy
- Risk Management, Economics, and Regulation
- Secure Design, Tooling, and Engineering
The only real hint at offensive was the final sentence of this paragraph:
“Military/defense. In 2010, Cyberwarfare became frontpage news, as well as a conspicuous reality with the Stuxnet attack on Iran (see page 14). Cyber security is crucial to the military and the Department of Defense both in terms of defensive/reactive capabilities, and in pro-active capabilities. Cyber defense is strongly related to resilience of the various critical infrastructures already mentioned above (Clarke and Knake, 2010). Additionally, forensics and attribution are fertile grounds for research involving many disciplines. However, in most advanced countries interest in a pro-active strike force is growing and more research and study is needed in this area.”
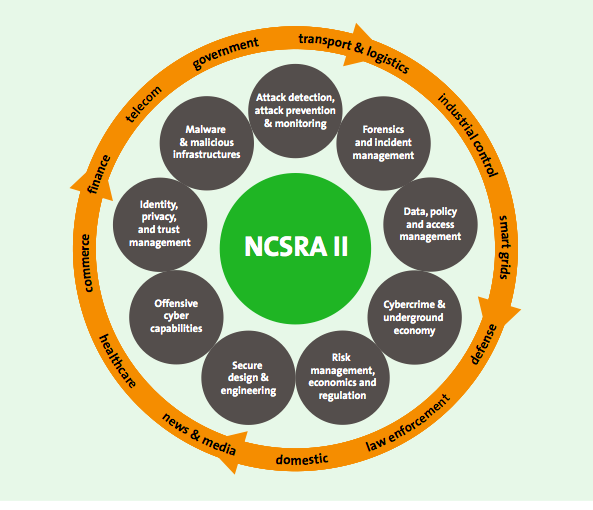
The new NCSRA-2 (2013) defines nine research themes, and now includes offensive (9th theme):
- Identity, privacy, and trust management
- Malware and malicious infrastructures
- Attack detection & prevention, monitoring [NEW]
- Forensics and incident management
- Data, policy and access management
- Cybercrime and the underground economy
- Risk management, economics, and regulation
- Secure design and engineering
- Offensive cyber-capabilities [NEW]
Concerning “Offensive cyber-capabilities”, the NCSRA-2 states:
“In some domains, it is important to develop techniques to strike back at attackers (both physically and by means of a cyber- attack). Besides the cyber-technical advances (often collectively referred to ’hacking back’), these include ways to disrupt financial and other support infrastructures on which the adversary relies. Offensive cyber capacities are equally essential in testing the defenses of existing systems – for instance in penetration testing.
Research challenges include the development of reliable techniques to penetrate other systems, evade defenses, and escalate privileges. Non-technical challenges include the development of legal guide-lines to determine when offensive capacities may be used and by whom, and against which targets. Decision procedures and command structures for the use of offensive cyber force are also areas that require research.”
The Addendum of NCSRA-2 elaborates:
“Operational cyber capabilities are becoming essential for defence organisations, but also in law enforcement and for prosecution. Law enforcement agencies have indicated an interest in offensive technology, not so much for ‘striking back’ at attackers, but with an eye on observing, disrupting and stopping criminal activities, as well aiding the apprehension of the perpetrators. This research theme focuses on improving the knowledge position and the operational cyber-capabilities in the widest sense.”
Possible research topics that are mentioned:
- Reliable and stealthy attack techniques
- Offensive countermeasures
- Cyber intelligence gathering methods and techniques
- Legal and ethical aspects of offensive cyber capacities and striking back
- Procedures and command structures for of cyber force
- Training capabilities for offensive cyber missions/serious gaming
- Damage assessment (including collateral damage)
- Integrated cyber and traditional offensive measures
- Command & control and governance of offensive cyber
- Ethical and legal considerations
- …
Disciplines that are mentioned:
- Computer science
- Criminal, ICT, and International law
- Law enforcement
- Military law
- Military strategy
- Organisation & Management
- …
One of the example short-term research questions:
“How can law enforcement agencies and/or the military obtain (develop/purchase) offensive technology?”
EOF