UPDATE 2011-08-21: Cryptome published “Wikileaks Public Relations Certified Ventriloquy” (.pdf, cryptome.org) (mirror)
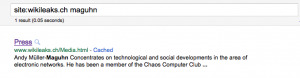
UPDATE 2011-08-20: It appears that the Google-cache for wikileaks.org/Media.html was updated on August 17th, and that that copy (already) not longer contains the name Andy Müller-Maguhn. I believe this means that Media.html was changed between August 13th and August 17th, and that Media.html may have been renamed to Press.html after that. This new information still ‘fits’ both the scenario of deliberate removal by WikiLeaks (with noble or less noble motivation) and the neutral scenario of coincidence. You can still see AMM’s affiliation (which has been mentioned on WikiLeaks.org right until the recent events around DDB) by searching Google for “site:wikileaks.ch maguhn”. Screenshot:
I solicited confirmations of this via Twitter: zero, one, two, three, four. If WL acted in bad faith themselves while aggressively attacking DDB’s integrity, that needs to be brought to light. For now I assume that WL removed AMM from the list because he has perhaps not been working with WL for a long time and that removing him from the list would prevent the kind of speculation that I’m doing here. Dear WikiLeak, clarify why the change happened at the time of DDB’s excommunication from CCC Berlin.
====== START OF ORIGINAL BLOGPOST FROM 2011-08-19 ======
Here’s an outsider observation:
- wikileaks.org/Media.html listed under “Wikileaks” CCC spokesman Andy Müller-Maguhn [1] but this page no longer exists — but it
doesdid in Google cache of August 13th 2011 23:46 GMT (this now shows August 17th copy, but here is my mirror copy of the August 13th version) [2] - wikileaks.org/Press.html looks *exactly* like Media.html but does not list Andy Müller-Maguhn (mirror copy of August 19th 13:00 UTC+2) [3]
I could not find any mention by WikiLeaks of this change (neither on Twitter, nor WLcentral, nor via Google search), although it seems highly relevant to ex-Wikileaks person Daniël Domscheit-Berg being kicked out of CCC(‘s Berlin chapter) (as told) by Andy Müller-Maguhn — which is said to have happened on the evening of Saturday August 13th (which also happens to be the time of the last Google cache copy mentioned above). The name may have been removed to prevent misunderstanding (=good), to cover a conflict of interest (=bad), or be coincidental. I’m not looking for trouble, but I’m too uninformed to know how to decide here and it is wasn’t me who started the Infinite Improbability Drive. I will update this blogpost to reflect advancing insight, including redress and apologies if it turns out I’m contributing FUD in stead of raising a reasonable doubt.
Also, the meaning of this all is perhaps modest; whether DDB is affiliated with CCC Berlin and whether there was any conflict of interest in those deciding on his CCC Berlin affiliation changes neither WikiLeaks nor OpenLeaks. But if the change was made to cover up conflict of interest, it does, IMHO, (slightly) level the playing ground between both as far as integrity is concerned.
[1]
“Andy Müller-Maguhn
Concentrates on technological and social developments in the area of electronic networks. He has been a member of the Chaos Computer Club since the early eighties and serves on its board. The main part of this work lies within the future-compatible structures and lifeforms and in the attempt to support those developments through transparency
andy@ccc.de”
[2]
irbaboon:~ monkey$ telnet wikileaks.org 80
Trying 178.33.255.46…
Connected to wikileaks.org.
Escape character is ‘^]’.
GET /Media.html HTTP/1.0
HTTP/1.1 404 Not Found
Server: Varnish
Retry-After: 0
Content-Type: text/html; charset=utf-8
Content-Length: 416
Date: Fri, 19 Aug 2011 11:07:27 GMT
X-Varnish: 2012796697
Age: 0
Via: 1.1 varnish
Connection: close
[3]
irbaboon:~ monkey$ telnet wikileaks.org 80
Trying 178.33.255.46…
Connected to wikileaks.org.
Escape character is ‘^]’.
GET /Press.html HTTP/1.0
HTTP/1.1 200 OK
Server: Apache/2.2.16 (Debian)
Last-Modified: Thu, 18 Aug 2011 11:47:51 GMT
ETag: “1e00a5c-6a64-4aac62eb987c0”
Vary: Accept-Encoding
Content-Type: text/html; charset=UTF-8
Content-Length: 27236
Date: Fri, 19 Aug 2011 11:06:57 GMT
X-Varnish: 2012796559
Age: 0
Via: 1.1 varnish
Connection: close