UPDATE 2017-05-23: reportedly (mirror: .html and .pdf) there is a longer-running partnership between the Dutch Defense Cyber Command (DCC) and the U.S. Army 780th Military Intelligence Brigade (aka ‘Cyber Brigade’). The partnership includes “sending U.S. cyber Soldiers and civilians to the Netherlands to attend the DCC Cyber Security Insight Course (CSIC)”. In October 2016, the Dutch participated in the “Bold Quest” training exercise at Fort Stewart, Georgia.
UPDATE 2016-11-30: the Dutch MoD announces that the DCC will be mission-ready in the first part of 2017; it has some 80 personnel, spanning defensive and offensive capabilities. (Note: that number represent just the DCC; obviously, more personnel with IT security knowledge and skills is present throughout the MoD, e.g. at DefCERT, Ivent and military intelligence.)
UPDATE 2016-06-xx: article, in Dutch, about the DCC: Defensie Cyber Commando, een nieuwe loot aan de defensieboom (.pdf, by BGen Hans Folmer, published in Intercom 2016-1, i.e., the magazine of the association of Dutch army signals officers)
UPDATE 2016-05-03: the Dutch MoD reports that it works with Thales to set up an advanced cyber training & test facility in the Du Moulin Barracks in Soesterberg.
UPDATE 2014-11-05: for illustrative purposes I added two tables on cyber vs physical/conventional topics from Cyberspace: The Ultimate Complex Adaptive System (.pdf, 2011) by Dr. Paul W. Phister Jr. (AF Research Laboratory, USA).
UPDATE 2014-10-23: added budget data, more context, and a chart from 2011 visualizing the implementation the Dutch Defense Cyber Strategy of 2012.
Colonel Hans Folmer, the Commander of the newly established Dutch Defense Cyber Command (DCC), wrote a short article (.pdf, in Dutch) for “Magazine Nationale veiligheid en crisisbeheersing 2014, nr. 5” entitled “The Dutch Defense Cyber Command: A New Operational Capability” (my translation). The magazine was published online by the Dutch government on October 22nd 2014. A translation of Folmer’s article follows in the body of this post.
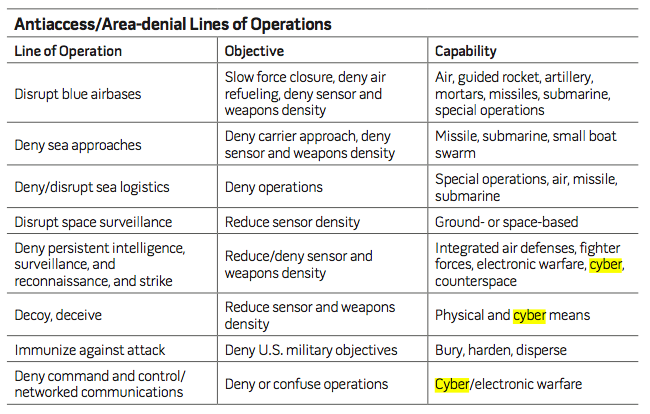
Cyber can be used by the military to carry out — with varying cost/risk/yield ratios — defense, attack and intelligence. For instance, to deny, disrupt, degrade or destroy enemy capability involving digital systems; whether on land, sea, air, space, or in the digital domain itself. To illustrate the use of cyber in the conventional military objective of antiaccess/area-denial, consider the following table published by Harry Foster, Deputy Director of the USAF Center for Strategy and Technology at Air University, in JFQ-72 (4.2MB .pdf, 2014):
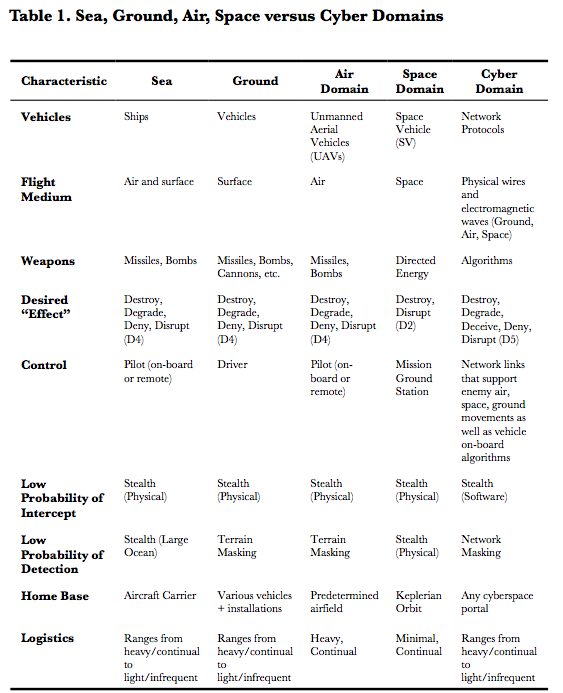
Two other illustrations can be found in Table 1 and Table 2 in Cyberspace: The Ultimate Complex Adaptive System (.pdf, 2011) by Dr. Paul W. Phister Jr. First, Table 1 maps the conventional domains — sea, ground, air and space — to the cyber domain:
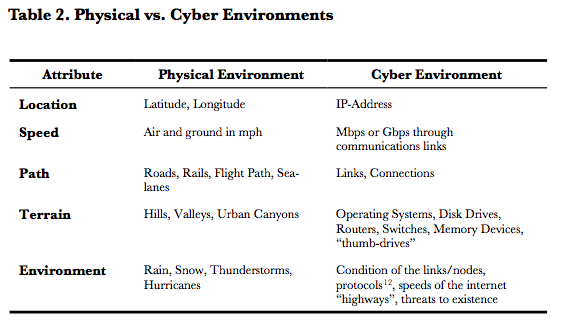
Second, Table 2 maps attributes of the physical environment to those of the cyber environment:
Now, on to the Dutch DCC. The Dutch DCC formally resides within the Royal Netherlands Army, the land forces element of the Dutch armed forces (in Dutch: “Commando Landstrijdkrachten” (CLAS)), but involves officers from all military domains. The DCC is primarily tasked with defense, but will also work on offense and, to a lesser extent, intelligence. The DCC will cooperate with the MIVD and the Joint Sigint Cyber Unit (JSCU). The JSCU is a joint organization of the General Intelligence & Security Service (AIVD) and the Military Intelligence & Security Service (MIVD) that is tasked with the collection of data from technical sources, making it accessible and searchable, perform analysis (correlation, data mining), and delivering sigint and cyber capability in support of the intelligence requirements of the AIVD and MIVD (possibly on-site in military deployment areas). Roughly put, the DCC is the Dutch smaller equivalent of USCYBERCOM, and the JSCU is the Dutch smaller equivalent of the NSA.
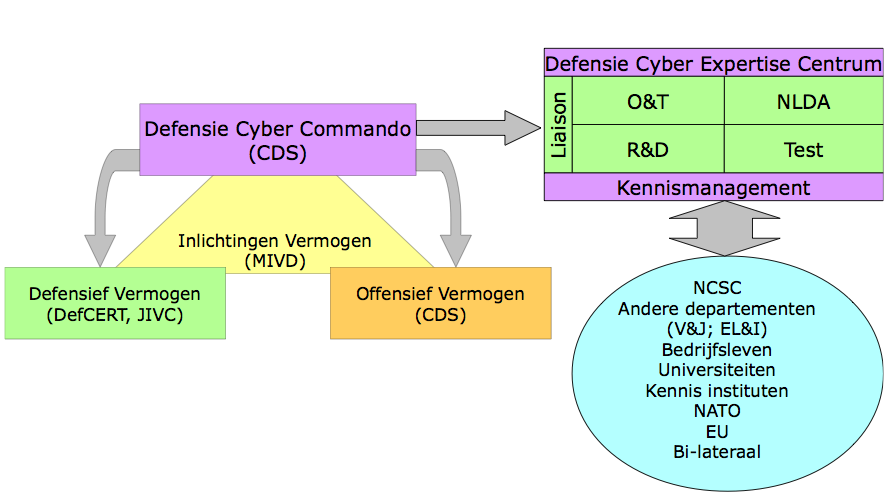
No organizational chart is available of the current situation (AFAIK), but in 2011, the following chart was used to visualize the implementation of the Dutch Defense Cyber Strategy, and still seems applicable:
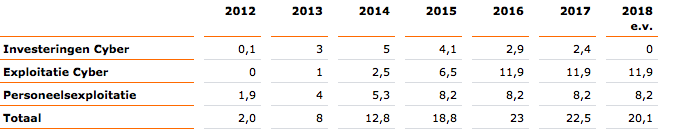
As of 2016, the annual budget of the DCC is estimated to be some EUR 21M. According to the budget (2.2MB .pdf, in Dutch) of the Ministry of Defense (MoD) for 2015, the investment budget for “cyber weapons” is EUR 5M in 2015, EUR 7M in 2016 and EUR 9M from 2017 onward. (Note: the document does not define “cyber weapons”.) The annual budget is divided in investments, exploitation and personnel as follows (in million euro):
Some 40% of this budget is assigned to the MIVD, some 40% to the DCC (including DCEC), and the remainder to Joint IV Command (JIVC), the Netherlands Defence Academy (NLDA) and Directorate of Operations (DOPS). The MIVD has some 800 employees, the AIVD has some 1500 employees. The JSCU will have 350 employees, mostly from the AIVD and MIVD. The number of employees residing under the DCC and DCEC is not known (to me), but it is reported that sixty new employees were acquired, and that fourteen military officers are will be trained in hacking by Fox IT.
Just like other parts of the armed forces, the operational use of the DCC will be controlled by the Chief of Defence (CHOD), the highest ranking military officer in the Dutch armed forces. This position is currently held by Tom Middendorp. (His predecessor, Dick Berlijn, has been Cybersecurity Advisor at Deloitte Netherlands since resigning in 2008.)
Here is a translation of Folmer’s article about the DCC (hyperlinks are mine):
The Defense Cyber Command, a new operational capability
By Colonel Hans Folmer
Commander of the Dutch Defense Cyber CommandOn September 25th 2014, the Minister of Defense, Jeanine Hennis-Plasschaert, established the Defense Cyber Command in The Hague. She rightfully called [.pdf, in Dutch] the launch of a new operational unit and the final addition of the cyber weapon to the toolkit of the Dutch armed forces a historic event.
The nature and character of conflicts change. Maximum disruption of societies increasingly is the objective of malicious actors. Increasingly, better use is made of modern, easy to obtain technical digital means.
In military operations, the cyber domain is used effectively by all parties both for command and control, and propaganda. Weapons and sensory systems are digital systems. Attacks can now occur globally and in real time. The enemy does not even have to physically cross a border to attack us. On the other hand, the enemy can be grabbed at large distance, or disruptive activities can be counteracted. It is of crucial importance to recognize, understand and control this, and also to deploy cyber weapons ourselves. The Dutch armed forces draws conclusions from this and wants to play the prominent role that suits our country. To guarantee the ability to deploy the armed forces and to increase its effectiveness, the Ministry of Defense has been working on strengthening its digital defensibility for several years, and will in the coming years be developing the capability to carry out cyber operations.
The establishment of the Defense Cyber Command (DCC) was the final step toward embedding all cyber capabilities within the Ministry of Defense. In June 2012, the Minister of Defense, Hans Hillen, presented the Defense Cyber Strategy. The core of the strategy is that the digital domain, next to land, air, sea and space, has now become the fifth domain for military action. Digital means as weapon or means of intelligence will increasingly be an integral part of military action. However, the dependence on digital means also results in vulnerabilities that require urgent attention.
The strategy includes six priorities that will guide the Ministry of Defense in effectuating hear goals in the digital domain:
- the establishment of an integral approach;
- the strengthening of the digital defensibility of the Ministry of Defense (“defensive”);
- the development of the military capability to carry out cyber operations (“offensive”);
- the strengthening of intelligence in the digital domain (“intelligence”);
- the strengthening of knowledge position and innovative capability of the Ministry of Defense in the digital domain, including the acquisition and retaining of qualified personnel (“adaptive and innovative”);
- the intensification of national and international cooperation (“cooperation”).
In the establishment of the strategy, the strengthening of our own protection was prioritized (by the establishment of DefCERT, the Computer Emergency Response Team of the Ministry of Defense) and expanding the intelligence capability. In addition, the knowledge position has been worked on energetically, with the establishment of the Defense Cyber Expertise Center [as per May 214], and of course on the cooperation with public, private and international partners. The establishment of an operational capability was originally planned for the end of 2015, but in the memorandum “In het belang van Nederland” the urgency was recognized and the establishment of the DCC accelerated.
The Defense Cyber Command is the central entity within the Ministry of Defense for the development and use of military operational and offensive capability. For that purpose, the DCC, in addition to a small staff, has three departments.
- The Operations department consists of a pool of cyber advisers for the support of operational units. These cyber advisers will be used in small teams during actual operational deployment and exercises, and are tasked with advising the operational commander on the use of digital means, dependency, vulnerabilities and capabilities of the enemies and our own troops. They will also advise on the protection of our own means. The cyber advisers are the link between the operational unit in the deployment area and the cyber units in the Netherlands (DCC and DefCERT). These teams will be trained jointly with operational units, as preparation for cooperation during an operational deployment.
- The Technology department consists of cyber specialists that have the technical knowledge and skills to act offensively in the cyber domain, both to carry out an effective defense as well as to support operations. Offensive cyber capabilities are capabilities aimed at influences or disrupting enemy actions. This concerns the development of (knowledge about) complex and high-tech means and techniques specifically aimed at increasing our own military capability. A cyber attack on an air defense system, for instance, can increase the effectiveness of an air raid, while limiting the risk to collateral damage.
- The Defense Cyber Expertise Center (DCEC) is the central entity within the Ministry of Defense for strengthening our own knowledge position, and as a result the innovative capability in the cyber domain. The DCEC will supply practically applicable cyber knowledge, concepts/doctrines and Education&Training support to all parts of the Ministry of Defense, and thereby contributes to the strengthening of the three cyber capabilities. The DCEC cooperates with knowledge institutions, universities and other (international) knowledge centers.
The mere establishment of the DCC does not yet achieve our goals. The establishment of this command will take time. In this domain, a new world is still to be discovered and developed. Much is yet unclear, and we are but at the beginning of the development of new capabilities. Existing tactics and methods of acting must be reshaped in the cyber domain. To that end, a cyber doctrine is currently being developed. Learn, experiment and apply, that is the motto for the coming years.
Summarizing, it must be possible to support military operations with offensive cyber capabilities. For that purpose, the Defense Cyber Command has been established. Offensive cyber capabilities can be a force multiplier, and thereby increase the effectiveness of the armed forces. By developing a robust cyber capability, the Netherlands can play an important role on this area within NATO. It is important that it is not a silver bullet to our all-encompassing vulnerability. It is, however, a crucial addition to our existing conventional capabilities on land, sea and air. Not a substitute, but a very important force multiplier.
Folmer states that the Netherlands “can play an important [cyber] role within NATO”. DefCERT has an existing covenant with NATO Computer Incident Response Capability (NCIRC). Also, one of the three NATO Communications and Information Agencies (NCI Agencies) is located in The Hague, adjacent to the business unit Defence, Safety & Security of knowledge institute TNO. According to some Parliamentary Papers, the MoD cooperates with TNO on the area of big data.
Furthermore, the MoD is a funding partner in Small Business Innovation Research Programs (SBIR) on cyber security. So far, two such calls exist: SBIR Cyber Security I (Sep 2012 – Dec 2014) and SBIR Cyber Security II (May 2014 – Jul 2016). Both involving some EUR 2-3M in available funding. A list of projects funded during the first call is available here. One of the example requirements the Dutch MoD expressed (.pdf, Jan 2014, in Dutch) in a pitch for SBIR-II is Linux/Python-built software for network reconnaissance against target networks for the purpose of identification, localization and detection; specifically also soliciting ideas for IPv6-based explorations.
Related:
- 2014-10-22: Offensive Cyber Operations in US Military Doctrine (Steven Aftergood’s blog)
- 2014-03-18: Progress of offensive cyber capabilities in the Netherlands’ armed forces (this blog)
- 2013-11-10: Offensive techniques in Dutch National Cyber Security Research Agenda II (NCSRA-2) (idem)
- 2013-09-25: Project Symbolon completed: the Dutch Joint SIGINT Cyber Unit (JSCU) is born (idem)
- 2012-07-18 The Dutch Defense Cyber Strategy (2012) (idem)
- 2012-07-17: Speech by Dutch Secretary of Defense at Cyber Symposium on June 27th 2012 (idem)
EOF
Thank you for this. Have been looking for information about the cybersecurity structures being created in The Netherlands. Really appreciate your translation of the articles you refer to into English.
The Netherlands, welcome to the neo-1984 state, where nothing you do is private, the only people that have privacy are the Politicians, Secret Services, Military and the Banks.
All other people are not important, and are seen as enemies of the Dutch rulers.
Secret courts can convict you and lock you up for live, with secret evidence you your self are not allowed to see.
Dutch democracy is completely fake ….. sadly most Dutch people have no understanding at all what is going on in their country, and cry and scream about the NSA, while their own country is a couple of magnitudes worse.
The AIVD always claimed to not intercept stuff on mass, but in reality they could always legally tap all the data that was send through the air.
Major internet connections are beamed through the air, ready for interception, like all the crap beamed from Rotterdam.
This new law only makes it simpler for them to now also go tap in to all the cables, nothing to see here move along.