UPDATE 2015-11-28: further updates moved to the bottom.
UPDATE 2015-07-09: addendum: Dutch intel oversight committee (still) seeks to publish statistics on use of special powers, suggests topics for debate on the new bill.
On July 2nd 2015, the Dutch government released (in Dutch) for public consultation the long-awaited bill (.pdf, in Dutch) + explanatory Memorandum of Understanding (MoU) (.pdf, in Dutch) that overhauls the Dutch Intelligence & Security Act of 2002 (aka “Wiv2002”). The bill is a complete rewrite of the current law (.pdf, in English), and includes expansions of power, as well as improvements to oversight, and new provisions for activities that the current law didn’t foresee (e.g. metadata analysis, small-scale use of DNA). Public consultation closes on September 1st 2015.
The post below covers, among others, the parts of the bill related to hacking and non-specific (‘bulk’) interception. First, some background.
The Wiv2002 covers both the General Intelligence & Security Service (AIVD) and the Military Intelligence & Security Service (MIVD). The cyber & sigint tasks are carried out by the Joint Sigint Cyber Unit (JSCU) that launched in June 2014. The JSCU is tasked with the collection of data from technical sources, making it accessible and searchable, perform analysis (correlation, data mining), and delivering sigint and cyber capability in support of the intelligence requirements of the AIVD and MIVD (possibly on-site in military mission areas). The JSCU will have some 350 employees. The Dutch Ministry of Defense established a Defense Cyber Command (DCC), which is affected by this bill to the extent that the DCC has relations with the MIVD or JSCU as part of its (military) tasking and operations. Roughly put, the DCC is the Dutch equivalent to USCYBERCOM, and the JSCU is the Dutch equivalent to the NSA.
Some background on the overall new interception framework — which is now divided in the phases collection, (pre)processing and analysis — is available here (note: that post was written on the basis of preliminary documents released by the government prior to release of the bill).
The approval requests that the services must send to the Minister prior to the use of most special powers are a primary source of information for legal oversight by the Dutch Review Committee on the Intelligence & Security Services (CTIVD). The CTIVD is an independent expert committee (not a court) that carries out its task on an ex post basis. For certain uses of special powers, the bill requires that the CTIVD be immediately informed by the intelligence service, and the CTIVD will then carry out an ad hoc review. If the CTIVD finds the approved practice to be illegal, the CTIVD can require the Minister to reconsider his/her decision; and then, if still necessary, inform the parliamentary standing committee on the intelligence services. The CTIVD has unrestricted access to information up to the highest classification (Dutch: “Stg. Zeer Geheim”, comparable to NATO Cosmic Top Secret), as well as to the AIVD’s building and employees. Regarding interception and hacking, neither the current law nor the bill include ex ante oversight or involvement of a court.
The non-specific interception power includes mandatory cooperation from (to be selected categories of) “providers of communication services” — a term that is defined in a way that includes not only providers of public electronic communications networks and services, but also providers of closed networks, and includes telcos, access providers, hosting providers and website operators. The use of this power requires approval from the Minister, and requires specification of the investigation (which can be long-running; think of non-proliferation and terrorism), the purpose of interception — “purpose-orientation” (Dutch: “doelgerichtheid”) is introduced as a new requirement that intends to limit bulk interception to what is relevant to a “purpose” that must be specified ‘as specific as possible’; a general indication does not suffice —, the type of telecommunications (e.g. GSM, radio, satellite, internet; optionally including geographic boundaries), optionally the types of traffic that are relevant (e.g. voice, chat, file transfer), and in the case of cable networks, the cable infrastructure that is targeted. In other words, no blanket authorizations for non-specific interception will exist, although blanket-like authorizations may, depending on how broad a “purpose”, in the context of a specified investigation, is allowed to be in practice; the requirement “as specific as possible”, mentioned in the MoU, leaves room for interpretation.
Specific interception, i.e., interception that only targets a specific individual, organization or technical characteristic (phone number, IP address, etc.), is omitted from this post, as that part of the law is not notably changed. The hacking power is included because it includes a new paragraph aimed at reconnaissance of computer networks (e.g. mapping computers and networks, running port scans, inquiring software/hardware configurations, etc.; think of GCHQ’s HACIENDA).
Now, moving on to selected texts from the bill and the MoU.
WARNING: the below contains unofficial translations. Feel free to contact me if you have questions.
The hacking power is pretty much unchanged, except that a specific provision is introduced for reconnaissance (Art. 30-1-a):
Article 30
- The services are authorized to:
- explore the technical characteristics of automated works that are connected to a communications network;
- whether or not using technical interference, false signals, false keys, false identity or through intervention of the automated work of a third party, access an automated work;
- The power meant in the first paragraph, under b, includes the power to:
- break any security;
- make technical provisions to undo the encryption of data stored or processed in the automated work;
- make technical provisions in relation to exercising the power meant in Article 25, first paragraph [=observation of persons], and Article 32, first paragraph [=specific interception];
- take over the data stored or processed in the automated work.
[…]
The MoU mentions that the power meant in the first paragraph, under a, will be used “semi-continuously” in order to detect relevant changes and keep an up-to-date picture of parts of digital infrastructure relevant to specific investigations. The MoU explains that the hacking power also includes the possibility of hacking a third-party system if a target’s own system cannot be directly broken into (as seen in Art.30-1-b):
The technical reality shows that targets are generally security-aware, but that operational opportunities for using weaknesses in technical peripheral users, such as co-tenants of a certain server, which can lead to successful breaking into the automated work of the target.
(Side note: to non-targets, some reassurance might be found in the following remarks in CTIVD oversight report 19 (.pdf, 2009) considering the interception of communication of non-targets, assuming its findings still apply today:
The AIVD can exercise a special power against a person in the (immediate) environment of the target, in order the obtain information about the target via this person (the non-target). The Committee considers this to be an extremely heavy means and finds that the AIVD must be very reluctant with its use. This means in not applied in large numbers and in nearly all cases in which the means is applied, the Committee finds that it is necessary as result of a threat to national security, because other means do provide insufficient insight into the target.)
The bill then introduces the term “provider of a communication service”, derived from the term “service provider” introduced in the Budapest Convention on Cybercrime (2001) (note: possibly, the official English translation of the Dutch law will mention “service provider”; I translated the text as literal as possible):
Article 31
In this paragraph and the provisions based thereon, the following definitions apply:
- provider of a communication service: the natural or legal person who, in carrying out their profession or business, offers users of the service the possibility to communicate via an automated work, or who processes or stores data for the purpose of such a service, or for a user of that service;
- user: the natural or legal person who has a contract with the provider of a communication service concerning the use of that service or who actually uses such a service.
[…]
From the MoU it is clear that “provider of communication service” at least includes providers of public telecommunication services and networks (public telcos and internet access providers) and providers of closed services and networks, as well as hosting providers (e.g. cloud) and website operators. The paragraphs cited below will apply to a “limited number” of such entities, in categories that will be determined by governmental decree.
(Side note: the term “automated work” is linked to the Dutch computer crime legislation. The Dutch government is preparing another bill that will grant police hacking powers. That bill won’t be released until after the parliamentary summer break, which ends on August 31st 2015. Some details available here.)
The intelligence services are granted the power of non-specific interception of “any form of telecommunications or data transfer via an automated work” (cable, ether, whatever; regardless of its source & destination, thus including domestic communication):
Article 33
- The services are authorized to, using a technical aid, wiretap, receive, record and listen to any form of telecommunications or data transfer via an automated work regardless of location in other cases than meant in Article 32 [= the specific interception power], if what has been required or provisioned by law is complied with. The power, meant in the previous sentence, includes the authority to undo encryption of telecommunications or data, as well as technical analysis of the data, insofar this is aimed at optimizing the use of the power meant in the previous sentence.
[…]
Article 34 provides the power to carry out sigint search/exploration on bulk-intercepted data (e.g. DPI, analyzing traffic flows, anomaly & signature based intrusion detection, etc.):
Article 34
- The services are authorized to carry out research using the data collected on the basis of the power meant in Article 33, for the purpose of:
- determining the characteristics and nature of the telecommunication;
- determining the identity of the person or organization related to the telecommunication.
- The services are furthermore, in the context of exercising the power meant in Article 35, second paragraph, authorized to carry our research on the basis of data collected on the basis on Article 33, for the purpose of:
- determining and verifying selection criteria related to persons and organizations or keywords related to topics of investigations;
- identifying persons or organizations, who in the context of ongoing investigations are eligible for being investigated by the service.
[…]
Note that the current sigint search power (Article 26 Wiv2002) is limited to communication that has a foreign source and/or destination. The above article in the bill no longer contains that restriction, thus enabling sigint search on domestic communications as well.
Providers of communication services can be required to hand over data that is needed to exercise the non-specific interception power (exercise of this power does not require separate approval from the Minister):
Article 36
- The services are authorized to request a provider of a communication service to provide data, which are necessary to exercise the power meant in Article 33, first paragraph. The categories of data, to which the request mention in the previous sentence can apply, will be determined by governmental decree.
[…]
- The provider of a communication service is required to comply with a request as meant in the first sentence of the first paragraph.
[…]
The MoU sheds a dim light on what data is meant in Article 36-1 (p.79):
[…] This involves acquiring information that can help map the communications landscape, which is necessary to, at some point in time, exercise the interception power meant in Article 33.[…]
[…] This involves, among others, the technical data of for instance the telecommunications network exploited by the provider, and the equipment used etc., which are necessary to — in consultation with the provider — determine what technical provisions that need to be made to carry out the authorized interception. […]
Footnote 63 of the MoU sheds slightly more light on this, and refers to the newly introduced requirement that interception must be purpose-oriented:
63: In order to intercept in a purpose-oriented manner, it must be made clear where, what type of communication is processed c.q. transported. This involves for instance information concerning business customers/tenants and data commonly known as part of daily operations of providers of communication services about the services offered, characteristics of traffic flows, and communication channels.
The data meant in Article 36 hence include data about the physical and/or logical layout of infrastructure, routing, signal properties, etc.
Providers of communication services must, at the request of the intelligence services as approved by the Minister, cooperate in enabling the intelligence services to exercise their non-specific interception powers, in that the providers must provide access to their systems/networks:
Article 37
- The services are authorized to request a provider of a communication service to cooperate in exercising the authorized interception as meant in Article 33, second paragraph.
[…]
- The provider of a communication service that is not already required to cooperate based on Article 13.2 of the Telecommunications Act, is required to comply with a request as meant in the first paragraph. The services are authorized to contact a provider of a communication service to request cooperation in the exercise of an authorized request as meant in Article 33, second paragraph.
- The provider must maintain, for twelve months, the technical provisions made as part of the requested cooperation as authorized per the second paragraph [= Ministerial authorization].
[…]
Per Article 132, not complying with an order is punishable as felony (if intent can be proven) or misdemeanor (if intent can not be proven). Page 202 of the MoU indicates that use of Article 37 will initially be limited to “several physical access points” (at telcos and/or internet exchanges):
(…) Partially to gain experience, on the basis of which more specific next steps can be taken, the interception will be limited to several physical access points in the first years after the law is enacted.
Raw bulk intercepts can now remain available for selection (by persons, organizations, technical characteristics and topic for keyword-based searches) three years instead of one year, as is presently the case. This increase is due to problems the services experience concerning (long-running) investigations into non-proliferation. Article 49 allows the services to share raw bulk intercepts — metadata and contents — with foreign intelligence & security services, under certain conditions, and only if approved by the Minister.
Providers of communication services can also be required, after approval from the Minister, to hand over users’ (stored) telecommunications contents (Art. 38; e.g. this is not a bulk power, telecommunications data can only be requested for a specified person, number, account, etc., such as the mailbox(es) of specified webmail users):
Article 38
- The services are authorized to contact a provider of a communication service to request data concerning the telecommunication of a user that has been stored by the provider as part of the communication service offered. The categories of data, to which the request mention in the previous sentence can apply, will be determined by governmental decree.
[…]
- The provider of a communication service is required to comply with a request as meant in the first sentence of the first paragraph.
[…]
Furthermore, the intelligence services are authorized, under certain conditions and after approval from their Minister (Art.30-6 and Art.41-2), compel anyone (Dutch: “een ieder”) — also including organizations — to help decrypt data in an automated work (Art.30-5 to 30-8) or help decrypt conversations, telecommunications or data transfer (Art.41-1), e.g. by handing over keys or providing decrypted data. (A similar provision is present in the current law.) Another legal option to defeat encryption is the use of the hacking power (Art.30, see below), which requires after approval from the Minister; and yet another legal option is the use of agents (who can be tasked with interception or hacking) or informants (e.g. a sysop who, as part of daily work, has access to cryptographic keys). Again, per Article 132, not complying with such an order is punishable as felony or misdemeanor.
New provisions are present concerning “automated data analysis” — think of metadata analysis based on non-specific intercepts:
Article 35
- The services are authorized to:
- select the data that have been collected through the use of the power meant in Article 33.
- apply automated data analysis as meant in Article 47 concerning data collected using Article 33 that concerns data other than the content of that telecommunication.
[…]
Article 47
- The services are authorized to apply automated data analysis concerning:
- data from the services’ own automated databases,
- data from information sources accessible to anyone,
- data from automated databases to which the services have direct automated access, and
- data from databases provided by third parties.
- For the purpose of processing the data meant in the first paragraph the data can at least:
- be compared in an automated way, or be compared in combination with each other;
- be searched on the basis of profiles;
- be compared for the purpose of tracing certain patterns.
[…]
In Article 47-2 the words “can at least” mean that the list (a, b, c) in Article 47-2 is not exhaustive. Concerning the profiling ex Art.47-2-b, the MoD states that hits found during automated profile matching must first be analyzed by a human before measures can be taken against the person(s) that match a profile. The “data from databases provided by third parties” (Art. 47-1-d) refers to databases that are provided voluntarily ex Article 22; there is no power to compel third parties (e.g. the private sector) to provide data(bases) in the way that US intelligence services can under FISA Section 215 on the basis of the “tangible things”-provision.
Lastly, Article 28 introduces provisions for the processing and storing of DNA by the intelligence services. This follows recommendations made in an oversight report concerning the lawfulness of the services’ (small-scale) use of DNA; some details available here.
The bill still restricts the use of the interception (non-specific and specific) and hacking powers to specific legal tasks, but a new task has been added for both the AIVD (‘g-task’) and MIVD (‘h-task’) concerning security screening of agents and informants (but excluding security screenings as meant in the Security Screenings Act (Dutch: “Wet veiligheidsonderzoeken”, or “Wvo”), e.g., the screening of candidate-employees of the intelligence services, defense industry, etc.). Interception is currently not permitted in that context. For the AIVD, use of special powers remains restricted to their security task (‘a-task’; think of national security) and their foreign intelligence task (‘d-task’; think of non-proliferation). For the MIVD, use of special powers remains restricted to their task concerning enemy forces (‘a-task’), their task concerning the Dutch armed forces (‘c-task’) and their military foreign intelligence task (‘e-task’). According to oversight report 38 (in Dutch), raw data from non-specific interception can not be used for the services’ other legal tasks, but evaluated data (i.e., data that has been processed and analyzed) can.
Article 18 limits — as does current law — processing of personal data by the services to specific categories of relevant persons (targets, persons voluntarily undergoing a security screening, etc.). But as the MoU explains, automated data analysis (e.g. metadata analysis) can involve processing data, e.g. collected via bulk intercepts, from other persons (non-targets) as well. And recall that raw bulk intercepts can be retained for three years.
Article 22 provides — as does current law (details) — the services permission to ask private parties (e.g. banks, public transport, or candidate-informants elsewhere) to voluntarily hand over data or databases, or make those accessible via automated means. The handover of personal data is exempted from Dutch Data Protection Act (“Wbp”). Article 22 combined with Article 35-1-b and/or 47 enables profiling, social network analysis etc. on the basis of voluntarily provided data; in addition to possible combination with data collected through other means, such as bulk interception, specific interception, and hacking. The related provision in the current law is used, for instance, in the context of tracking terrorist’s finances. Requests for data can be made only in the context of a specified purpose/investigation; the MoU states: “arbitrary requests for data are not allowed”.
Someone told me the bill seems quite polarizing; indeed, there are a lot of “musts” present, and the definition of “provider of a communication service” is very broad. But further things are relevant to assessing the bill as a whole:
- the proposed (permanent) five-year mandatory re-examination of the law (Article 147);
- the proposed introduction of required “purpose-orientation”, which intends to limit the hay stack created using non-specific interception to relevant information. The MoU mentions that “filters” will be used to filter (ir)relevant data;
- caveat: it remains to be seen what filters will be applied (filters for volume reduction? of course; filters for privacy? only if possible) and how broad a “purpose” can be defined for the collection phase and the (pre)processing phase in the new interception framework;
- the proposed provisions that provide new ways of reporting wrongdoing (Article 114-120). The provisions extend to ‘anyone involved in the exercise of this law’ (including e.g. employees of providers) and cover reporting violations of law, dangers to security, and dangers to the proper functioning of “the public service” (the latter is mentioned in Article 114-c but not explained in the MoU; presumably it refers to the intelligence service);
- the proposed mandatory reporting about the use of special powers (Article 45);
- caveat: related existing requirements have not always been met in the past;
- the proposed limitations on retention of intercepts — raw bulk intercepts can be stored for three years ex Art. 33-5, irrelevant yields of hacking, specific interception and obligated telecoms data hand-over can be stored for max 12 months ex Art. 30-9, 32-10 and 38-7;
- caveat: encrypted data obtained via non-specific interception can (still) be stored indefinitely; the retention period does not start until the data is decrypted — think of collecting TLS-encrypted traffic until you know what to do with it (possibly compel someone to decrypt it or hand over keys). Also, raw bulk intercepts can now remain available for selection three years instead of one year, as is presently the case;
- the proposed specification of information that must be present in approval requests sent to the Minister. Concerning bulk interception, the MoU states that the approval request must specify the relevant ongoing investigation, the purpose of the requested interception (that must be specified ‘as specifically as possible’; ‘a general indication does not suffice’), the type of telecommunications (e.g. GSM, radio, satellite, internet; ‘possibly’ including geographic boundaries), ‘possibly’ the types of traffic that are relevant (e.g. voice, chat, file transfer), and, in the case of bulk cable interception, the cable infrastructure that is targeted.
- caveat: it has always been required that approval requests include a motivation (in terms of necessity, proportionality and subsidiarity), but oversight reports show that it has often been missing or was inadequate in the case of the use of the existing (ether-only) sigint power — which is why I stated oversight is currently broken. The new bill aims to fix that (e.g. through the new three-phase interception framework, and by no longer requiring separate approval requests from the Minister prior to selecting persons, organizations, characteristics or keywords from raw bulk intercepts), but we won’t really know what has (not) been fixed until the bill is adopted and new oversight reports are published based on the new legal framework;
- the proposed increase of the level of authorization required for hacking (ex Art.30-3) and sigint search (ex Art.34) from head of service to Minister;
- caveat: the risk of rubber-stamping remains a point of attention, because — as is clear from past oversight reports and parliamentary papers — the Minister usually has a lot of approval requests to decide on. In fact, the number of requests is likely to increase as result of the heightened approval regime for various (old and new) powers; although sigint selection (selecting data about specific persons, organizations, technical characteristics, or keywords from raw bulk intercepts) no longer requires separate, per-case approval from the Minister;
- the many other proposed changes concerning oversight — but alas, still no ex ante or court oversight —, complaint handling, aspects of freedom of information, and more.
The compelled-decryption provision laid down in Article 41 references, in Article 41-1, the non-specific (‘bulk’) interception power laid down in Article 33-1. If I’m interpreting the bill and MoU correctly, this permits the Minister to compel organizations (such as providers) to decrypt data or hand over keys also for the purpose of exercising the non-specific (‘bulk’) interception power. Think of requiring handover of TLS keys used on shared servers, cloud CDNs, or crypto used to protect links between data centers. If this is indeed in scope of the law, then that’s probably a topic for debate — regardless of the fact that page 202 of the MoU indicates that use of the compelled-access power will be limited to “several physical access points” in the initial years, and without leaving this up to assumptions about whether the intelligence services will or will not apply the law this way, and whether the Minister and CTIVD would approve in specific cases.
Appendix 3 of the MoU provides an overview of all powers and safeguards in the bill:
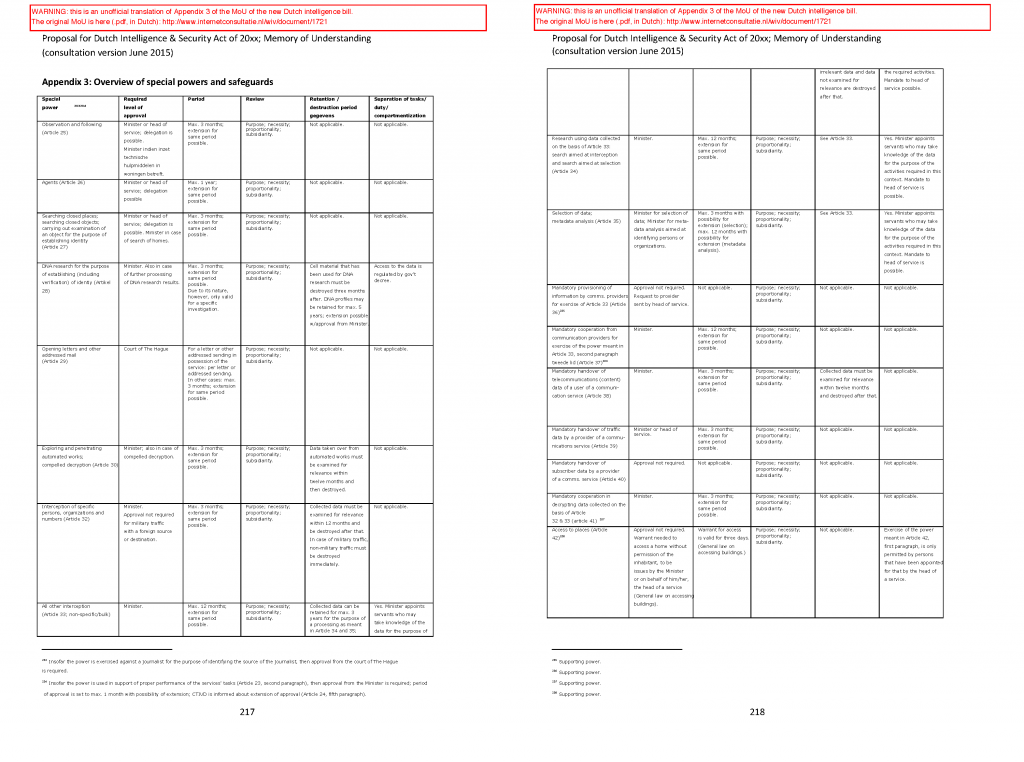
(Also available as .pdf here.)
UPDATES (new to old)
UPDATE 2016-04-29: the confidential revised draft + MoU that the Dutch government submitted for advice to the Council of State was leaked via Dutch newspaper Volkskrant. An analysis by Bits of Freedom is available here (in English). I posted some notes on my blog here and here (both in Dutch).
UPDATE 2016-04-15: an additional NOS report states that the existing (targeted) interception power and (targeted) hacking power, too, will be subject to ex ante and binding oversight. The newly to be established oversight committee is entitled ‘Toetsingscommissie Inzet Bevoegdheden’ (TIB), and will consist of persons that have a background in the judicial branch.
UPDATE 2016-04-14: NOS reports that according to unnamed sources, the Dutch government will, with regard to the upcoming cable interception power, consider ex ante oversight by a new independent committee. (Note: ‘new independent committee’ presumably means it’s not about the CTIVD, the existing independent expert committee that has been carrying out ex post non-binding oversight since 2002.) Furthermore, requiring prior court approval for the interception of communications of lawyers and journalists will also be considered. The report states these topics will be discussed in the cabinet. The cabinet changed “purpose-oriented interception” (my translation from the Dutch word “doelgericht” used previously) to “investigation-bound interception” (my translation of “onderzoeksopdrachtgericht”). It’s just different words for the same thing: interception that is carried out in the context of an intelligence task, but that is not targeted/limited to specific known persons or organizations.
UPDATE 2015-11-11: the transcription of a parliamentary debate of September 2nd 2015 on intelligence affairs, including the draft bill, is now available here (in Dutch). When the cabinet submits the revised bill to the House of Representatives (lower house), the house will also receive the Privacy Impact Assessment (PIA) performed on the draft bill by PI.lab (a cooperation between Radboud University, Tilburg University, SIDN and TNO) and coordinated by professor Bert-Jaap Koops.
UPDATE 2015-11-04: the oversight committee (CTIVD) published its response (in Dutch) to the draft bill. An English outline of that response is available here.
UPDATE 2015-10-21: the current progress of the bill within the legislative process can be viewed at the ‘live’ webpage here (in Dutch). The bill is currently at the end of the preparatory phase: public consultation closed on September 1st, and the government is now processing the public comments. Next, the government will submit the bill, possibly changed as result of public comments, to the Council of State for advice. Then, the government will submit the bill, possibly changed as result of the Council’s advice, to the House of Representatives. If the bill is adopted by a majority vote of the House, the bill, possibly changed, will be submitted to the Senate. If it is adopted by the Senate, the law and a date of enactment will be published. Conceivably, whatever the new law will look like, it seems likely it won’t be enacted before 2017.
UPDATE 2015-07-23: today, three weeks after publication of the bill, legal scholars from the University of Amsterdam published a report (.pdf, in English) entitled “Ten standards for oversight and transparency of national intelligence services”. Short write-up here. Notably, the authors of the report plead for ex ante review of interception and intelligence operations by a court. The bill neither includes independent ex ante review, nor any court involvement.
EOF
